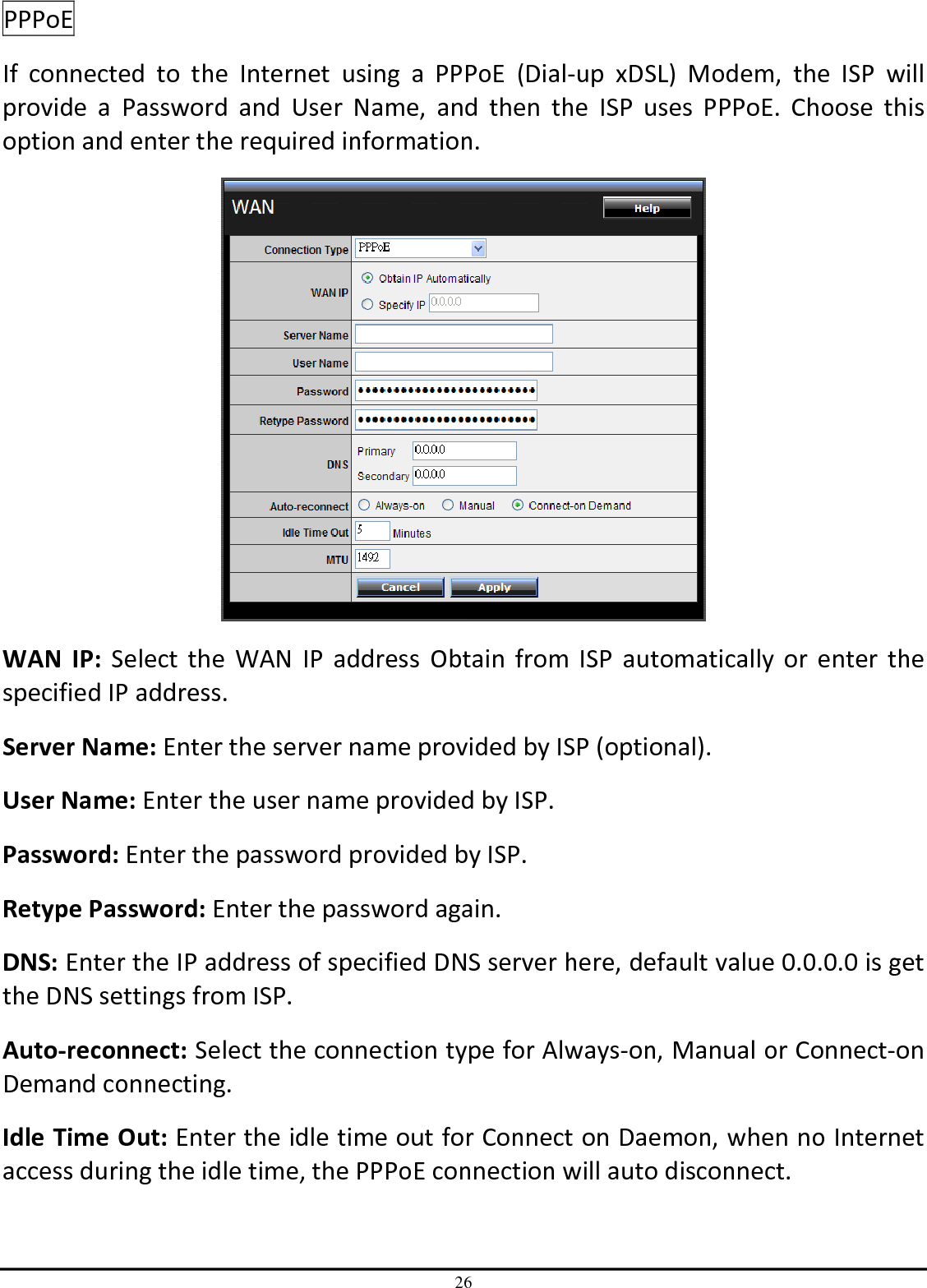
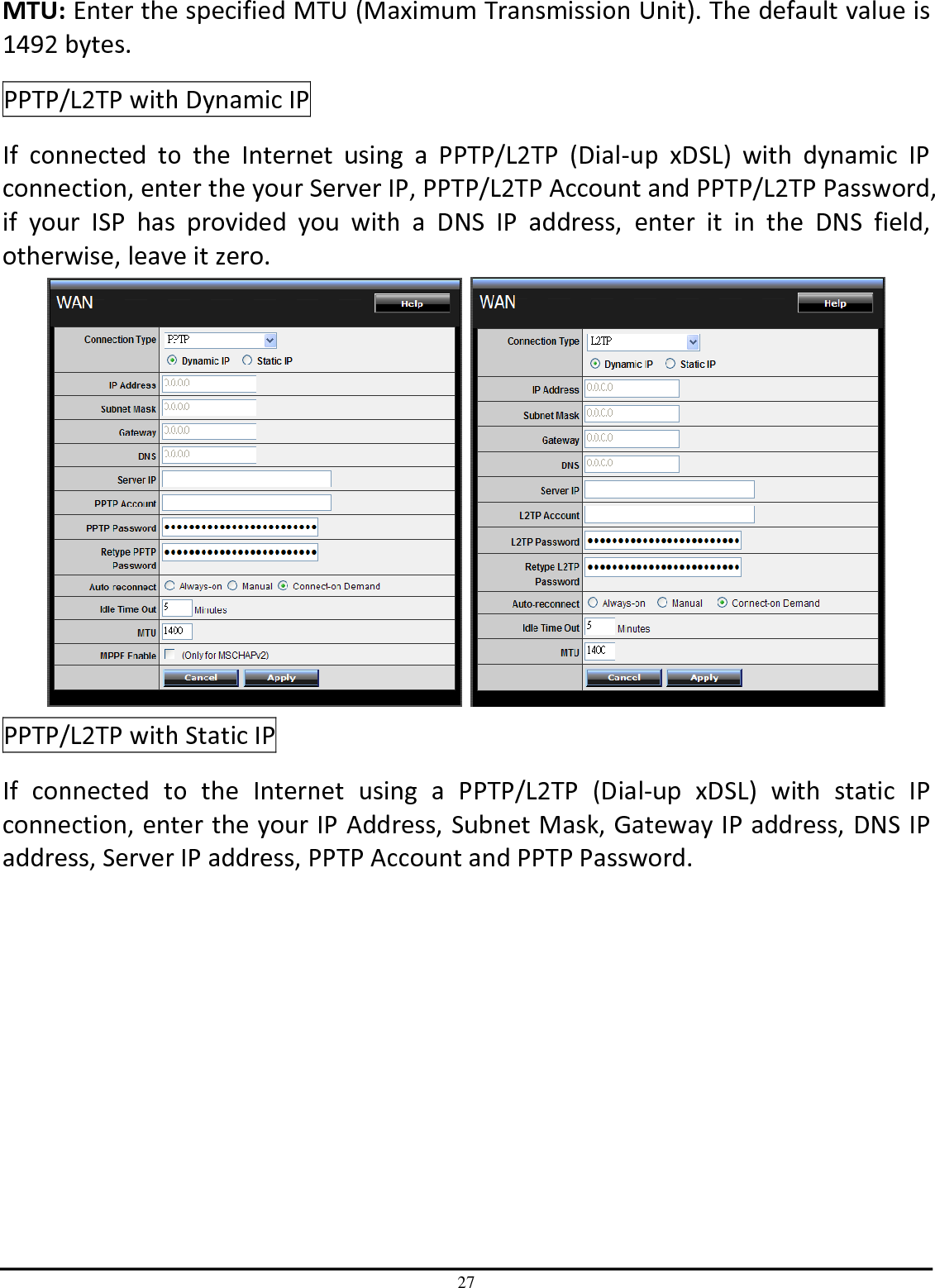
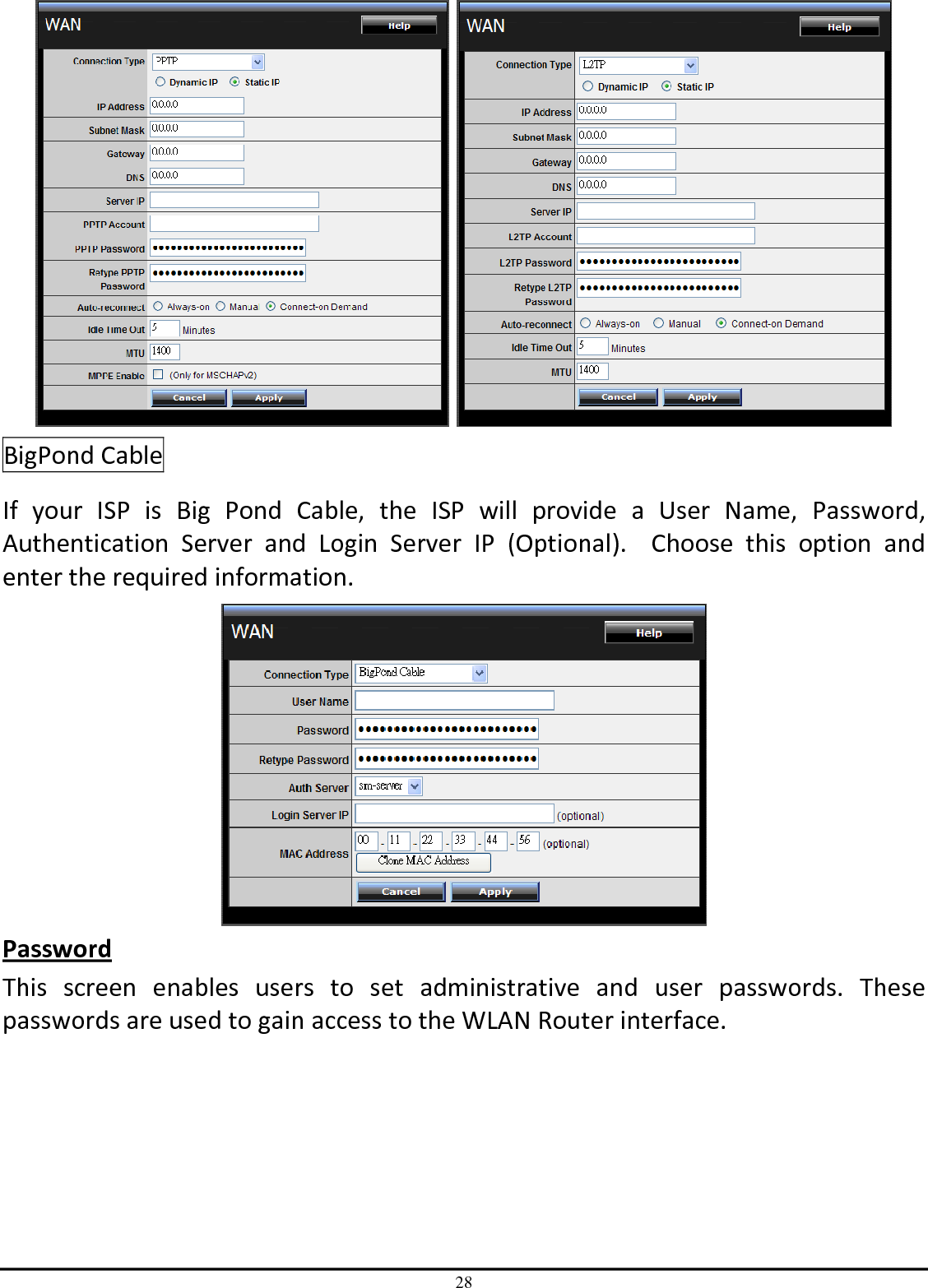
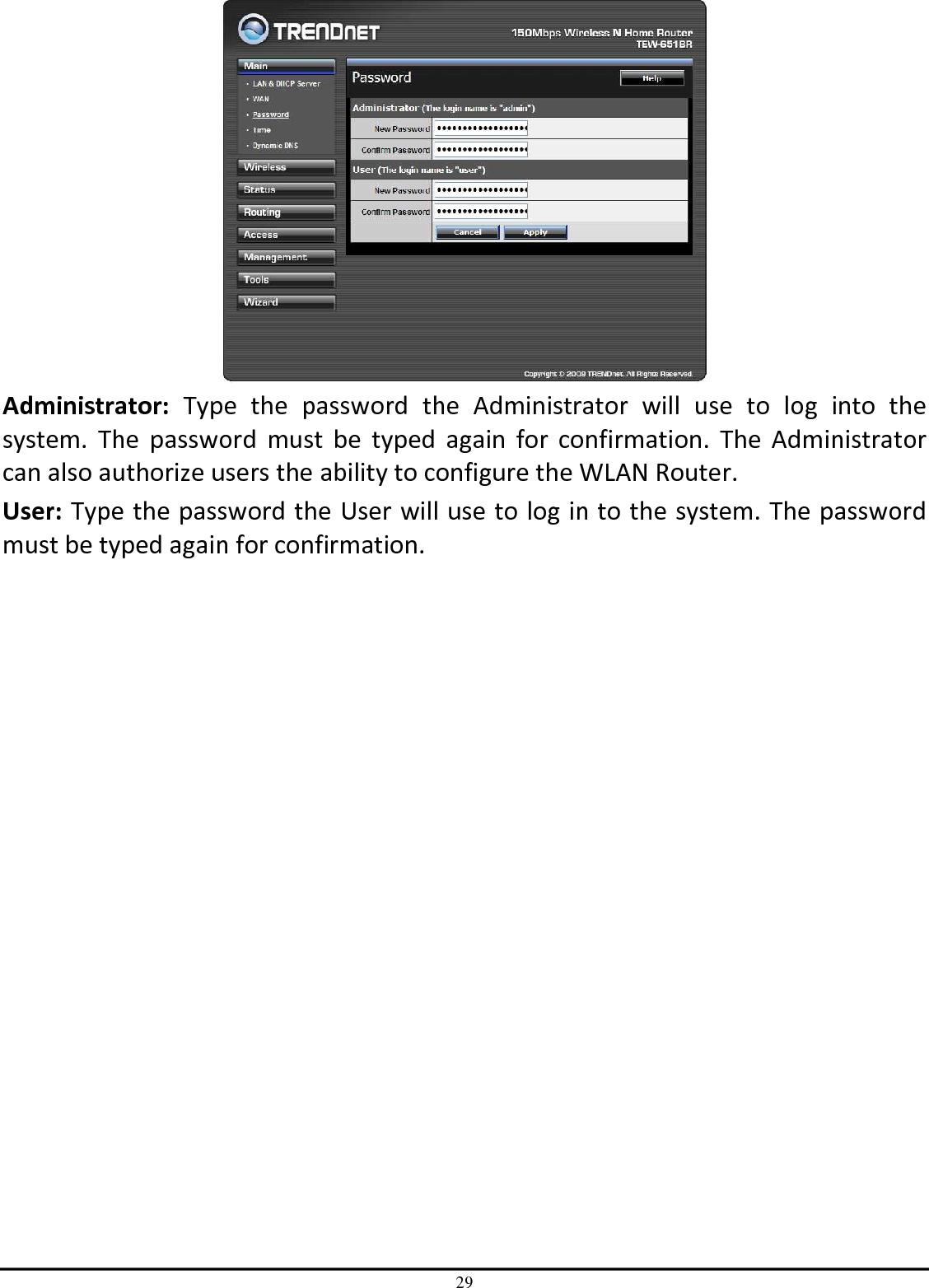
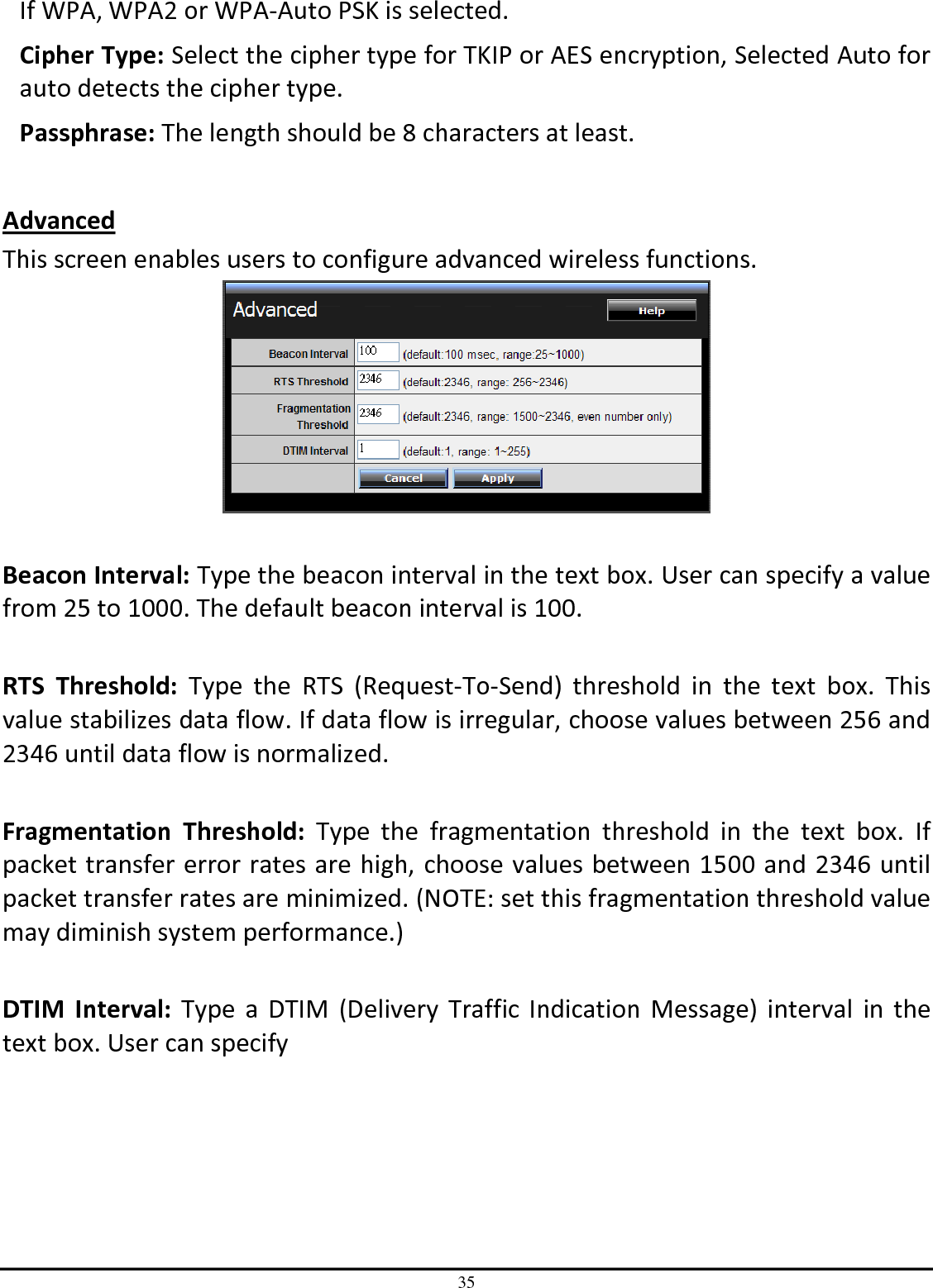
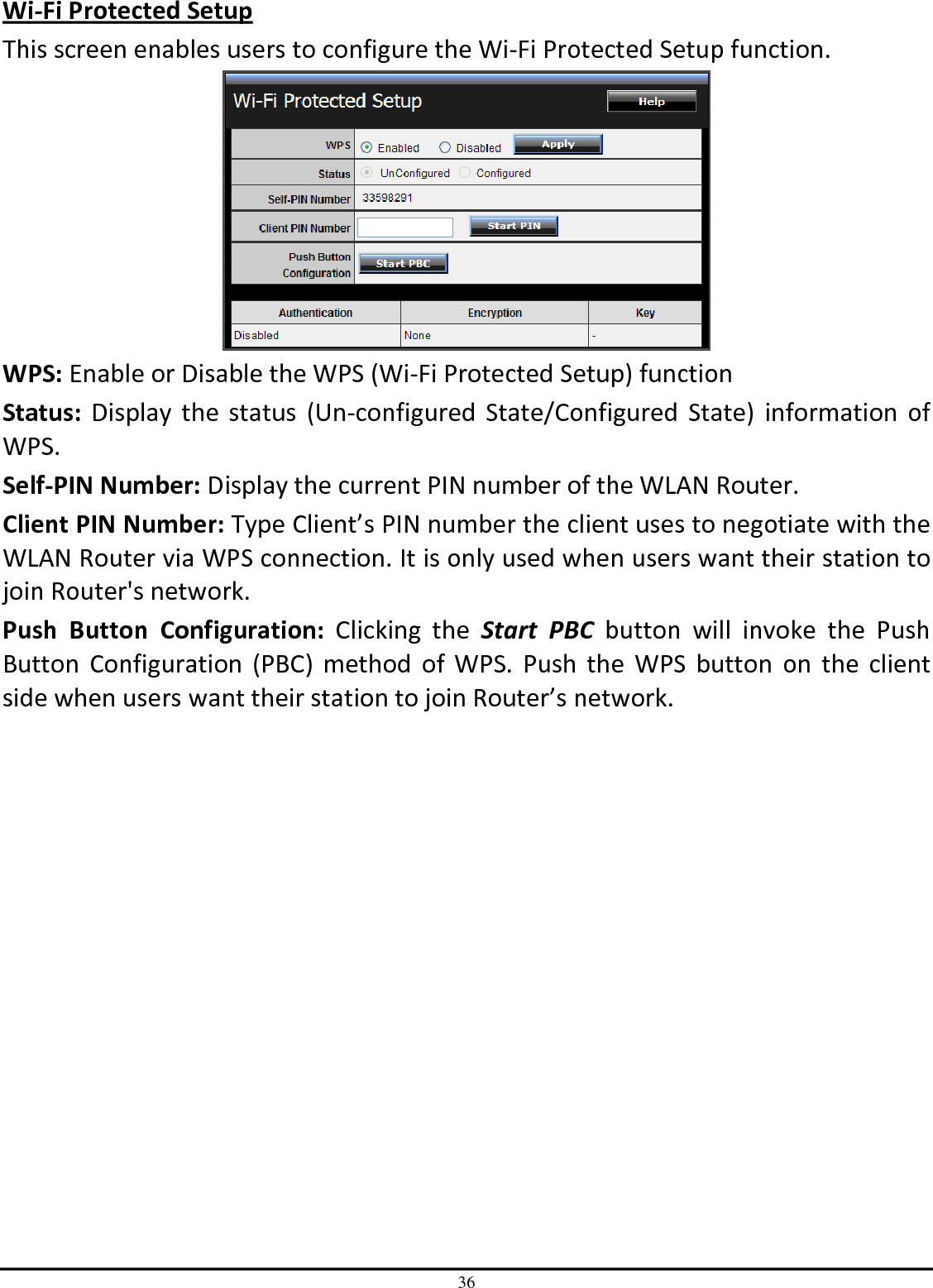
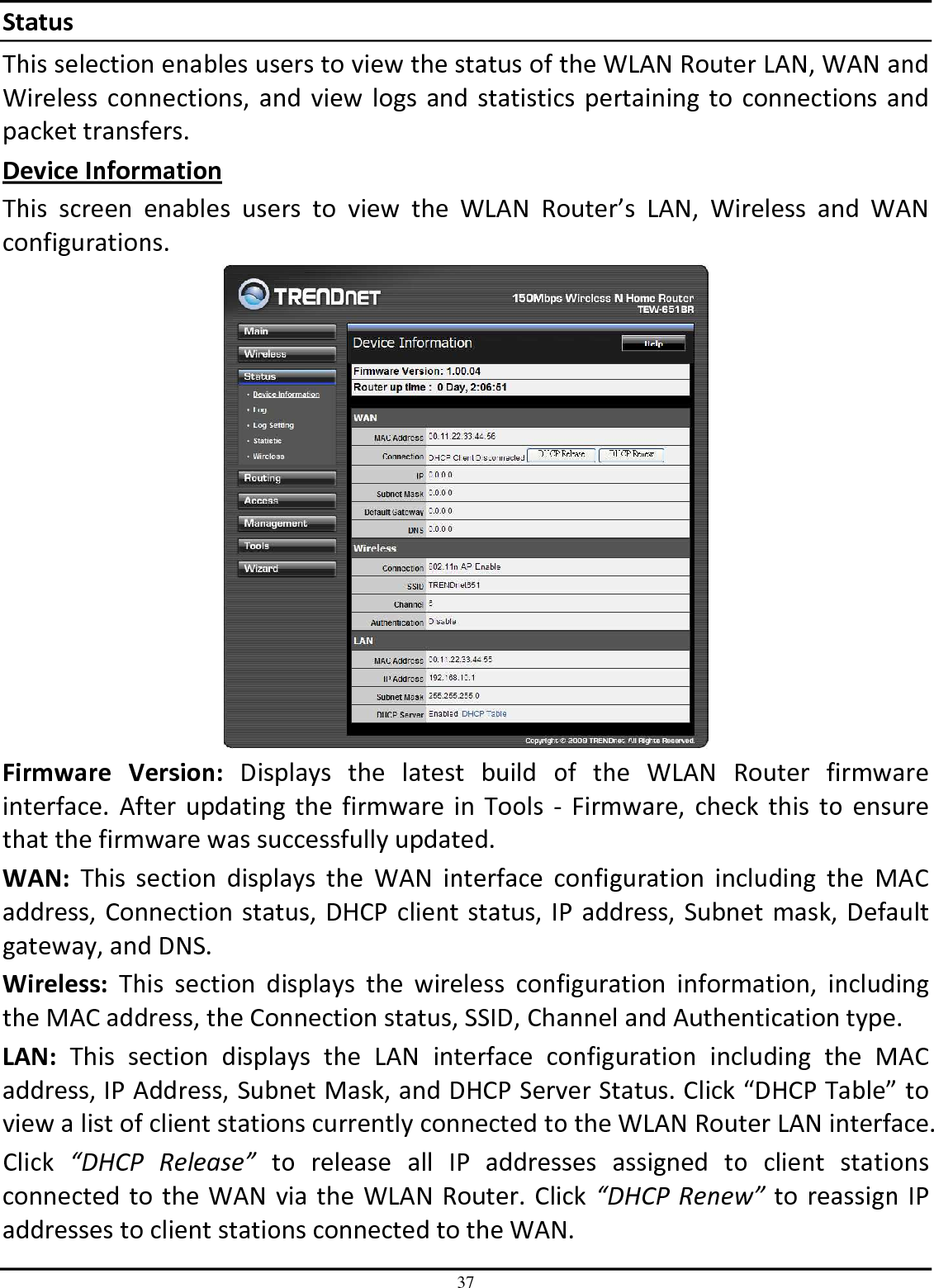
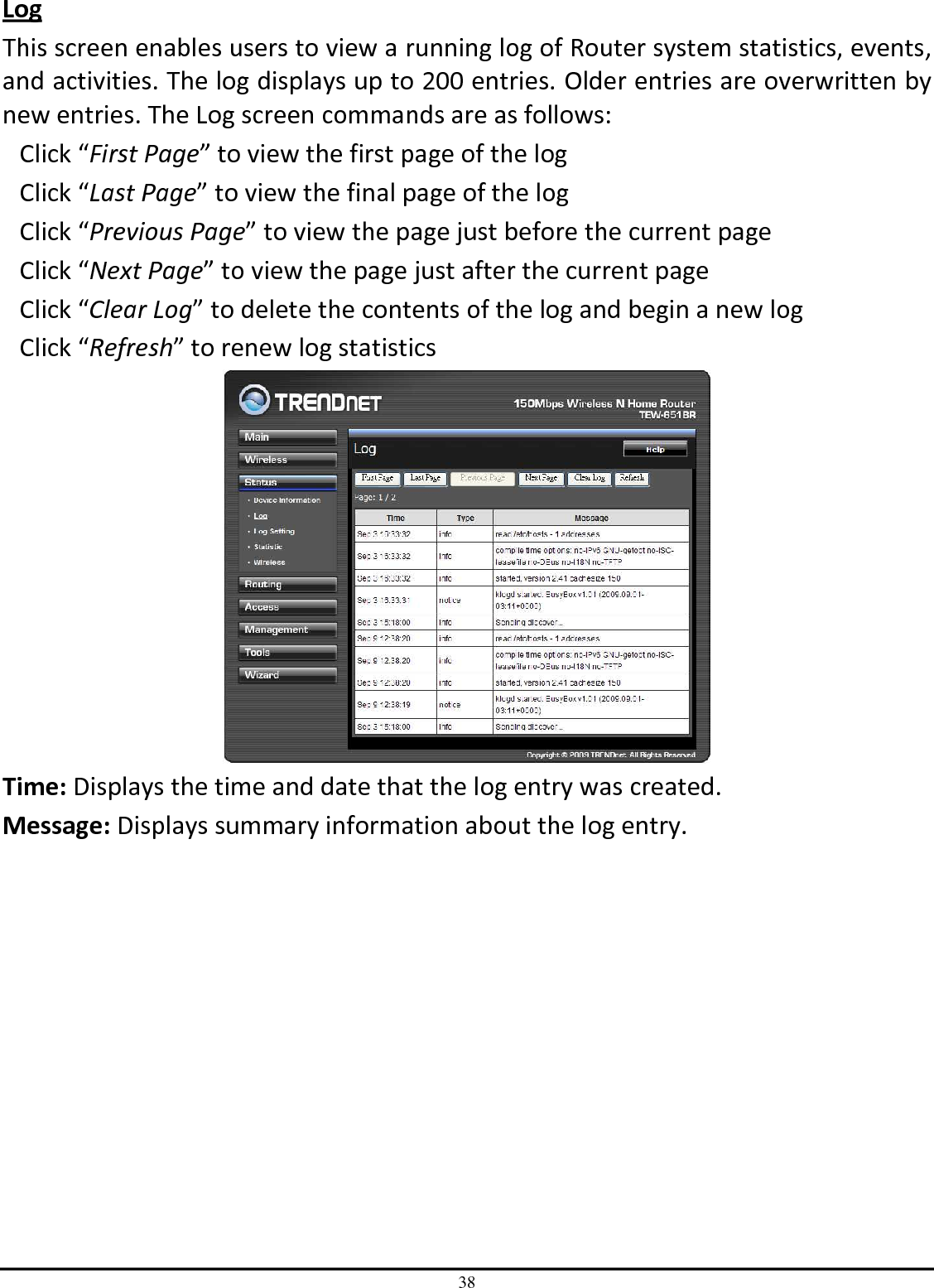
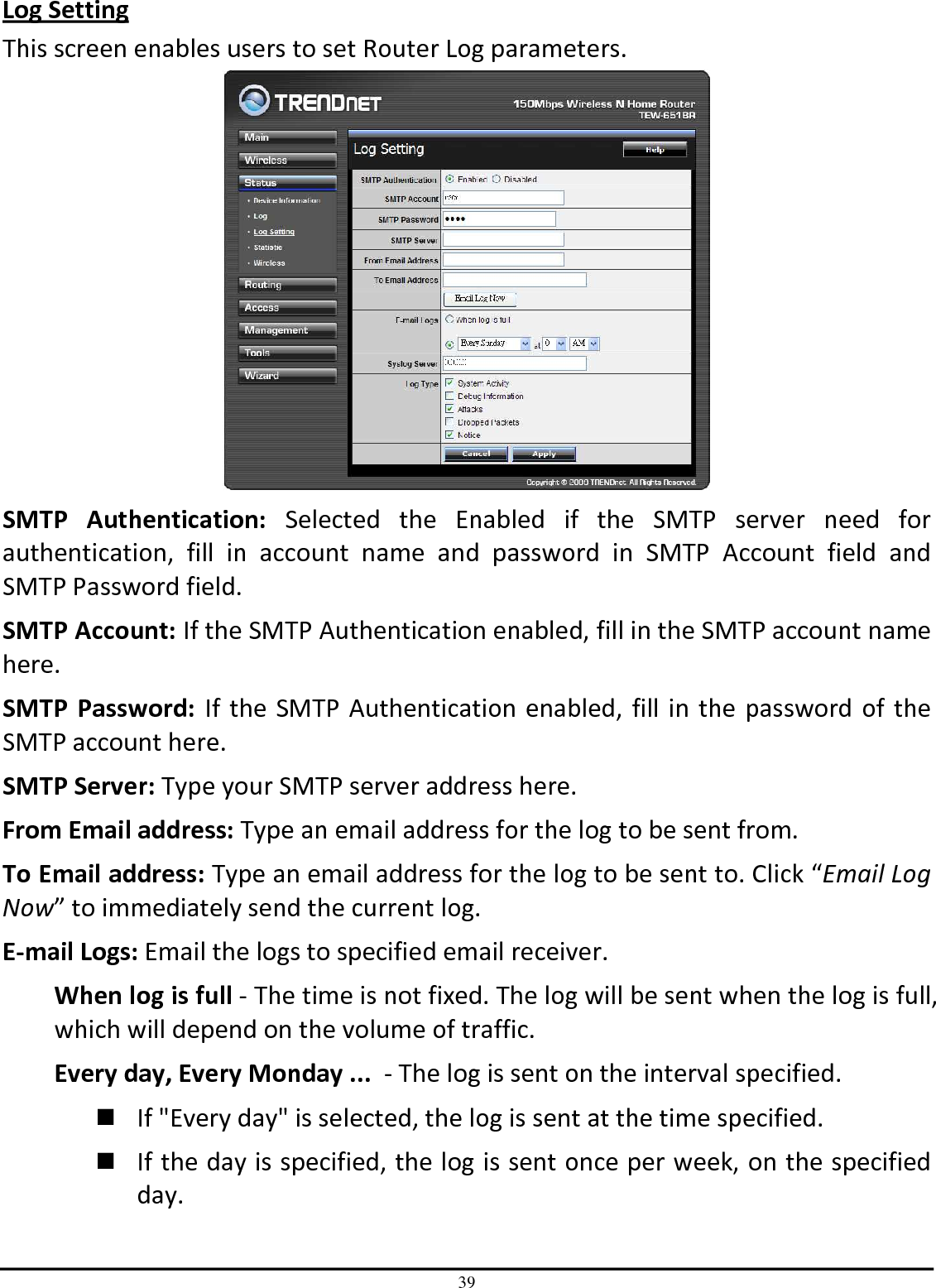
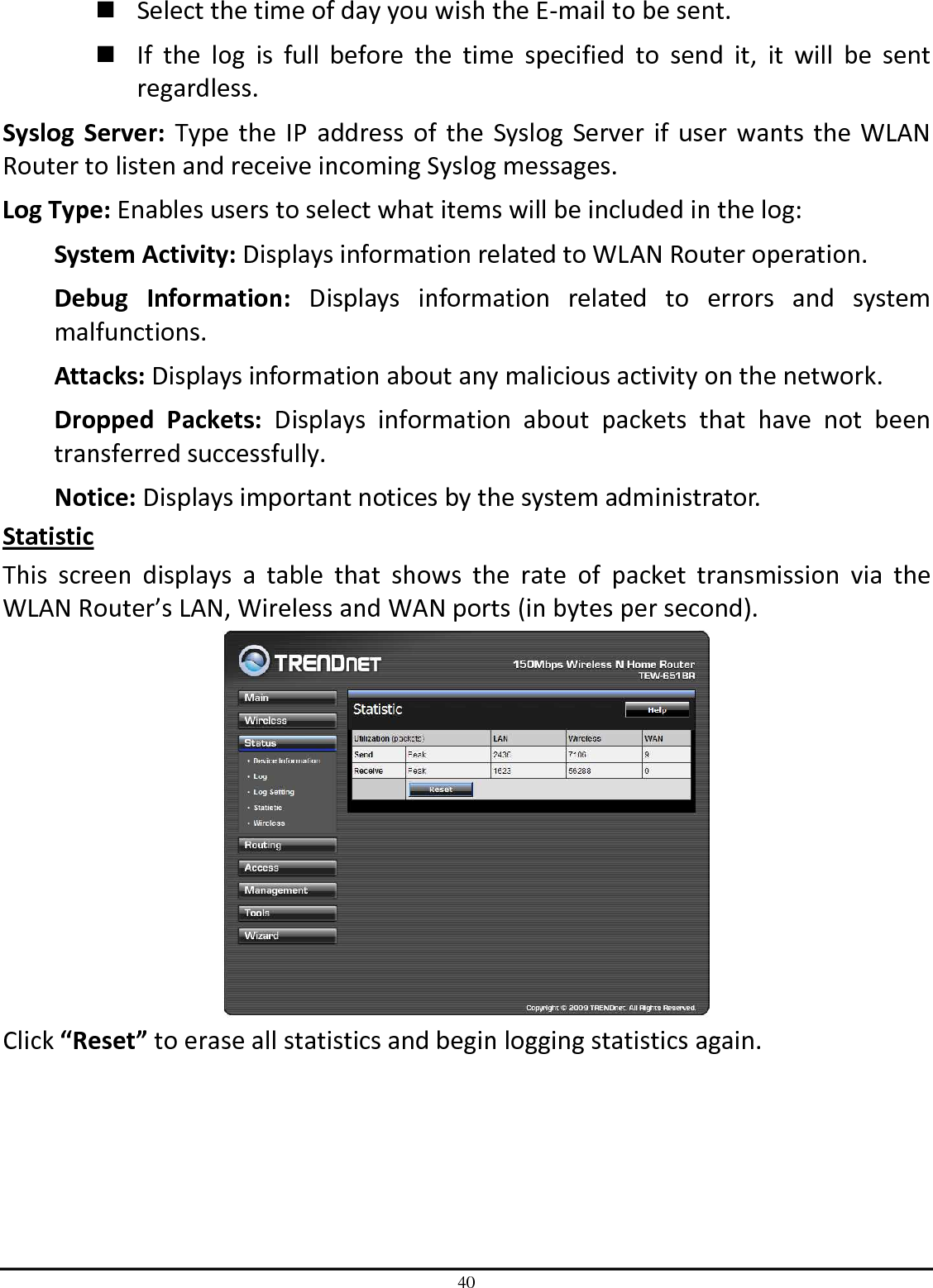
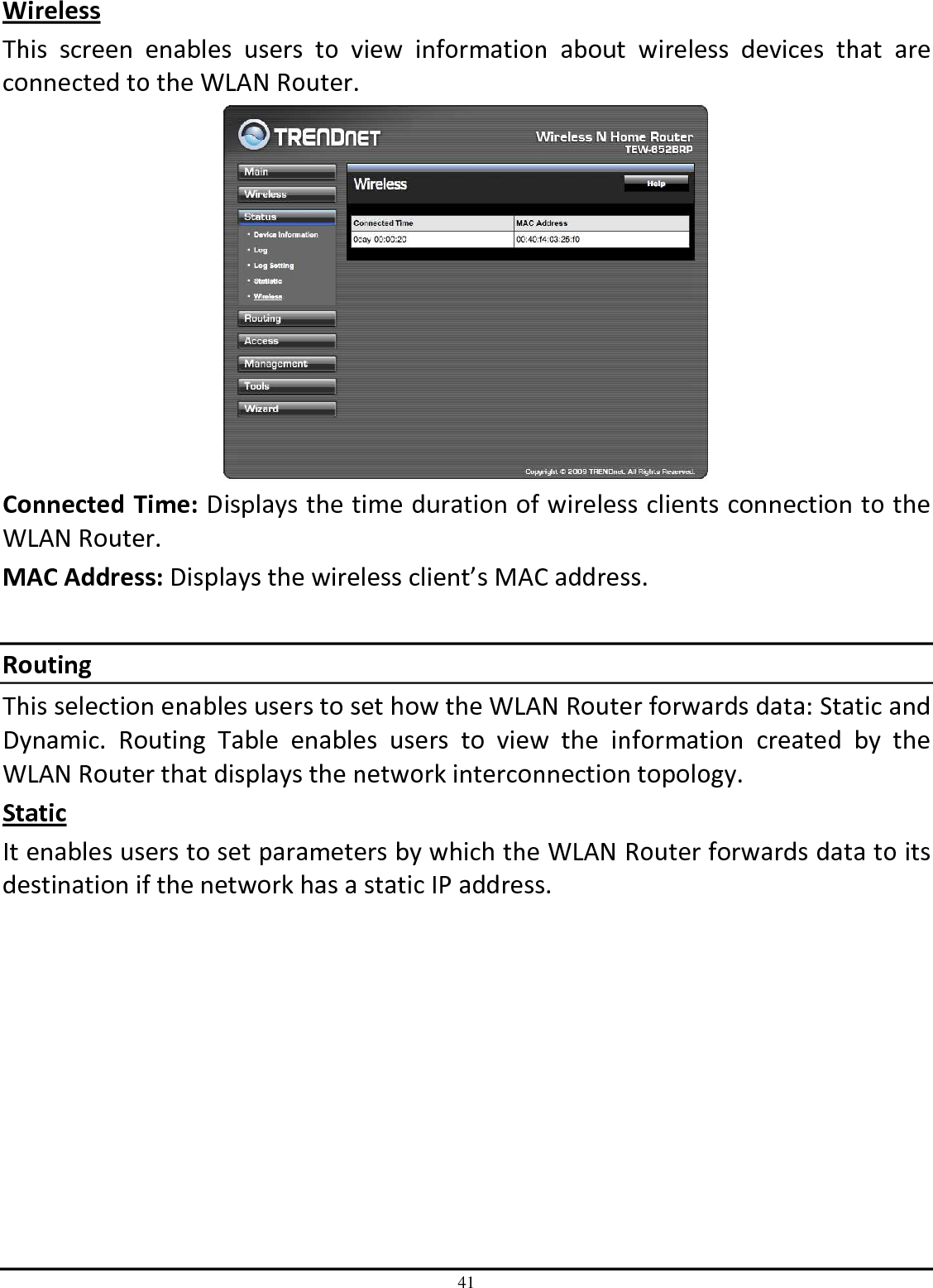
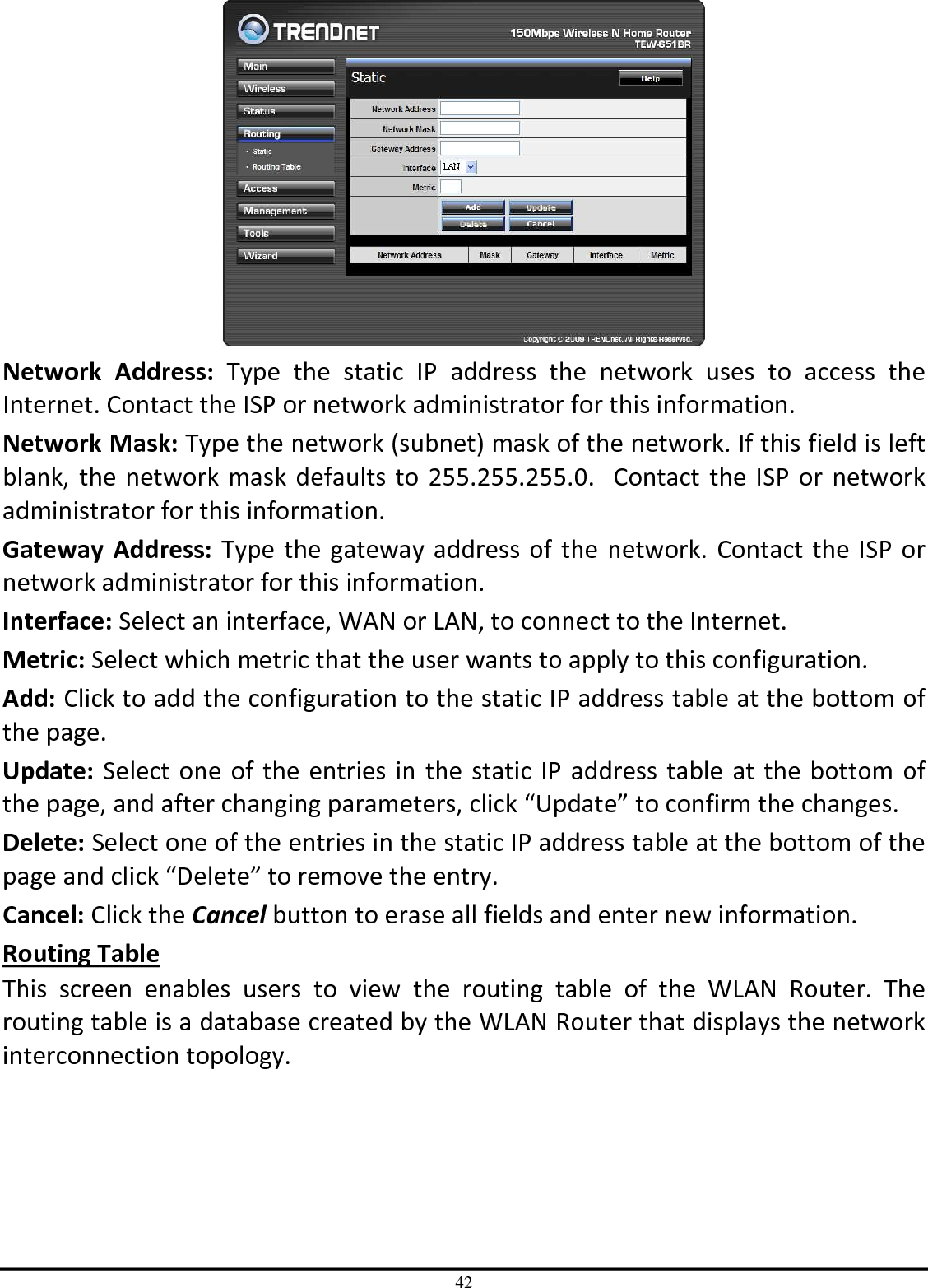
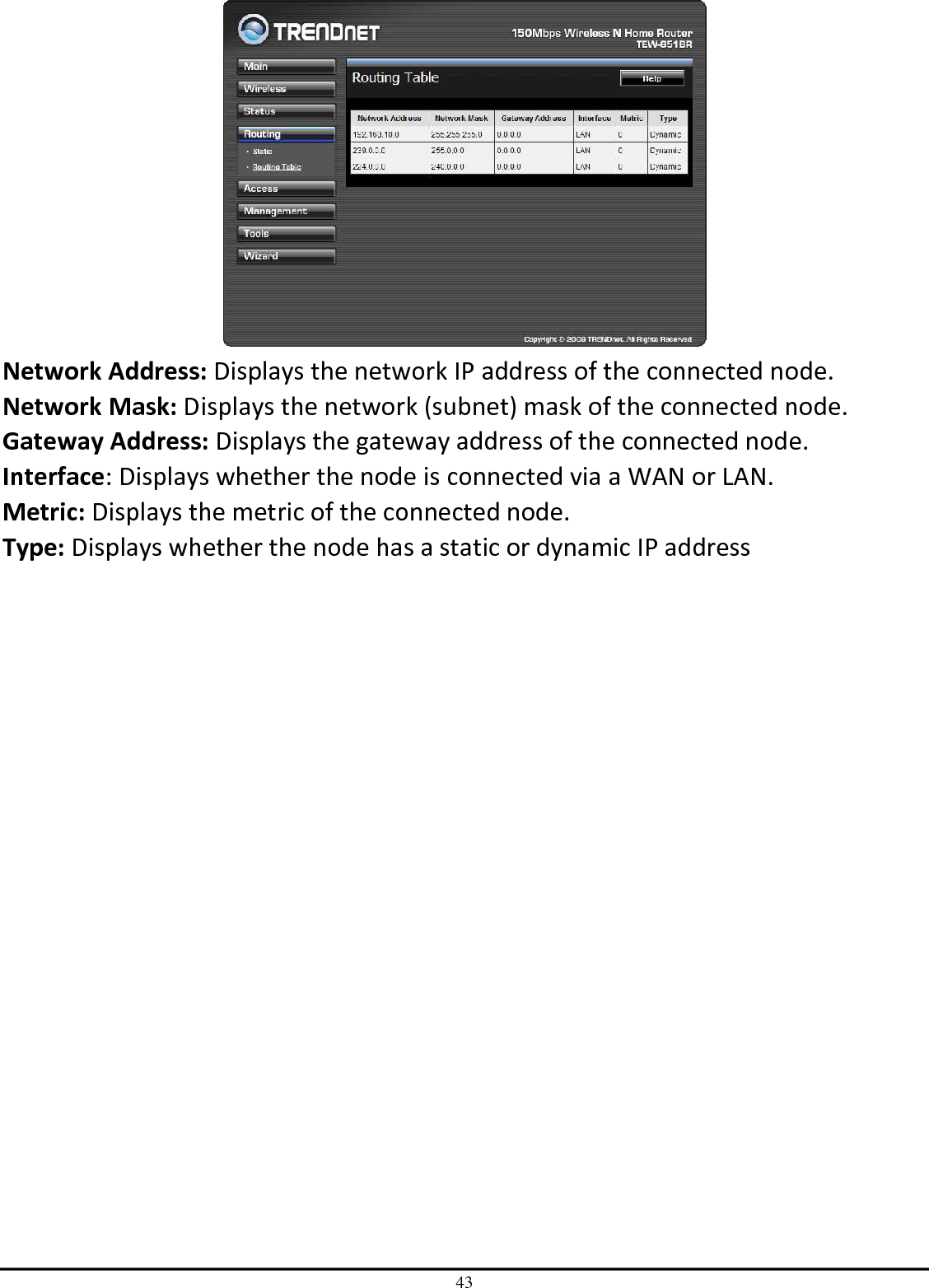
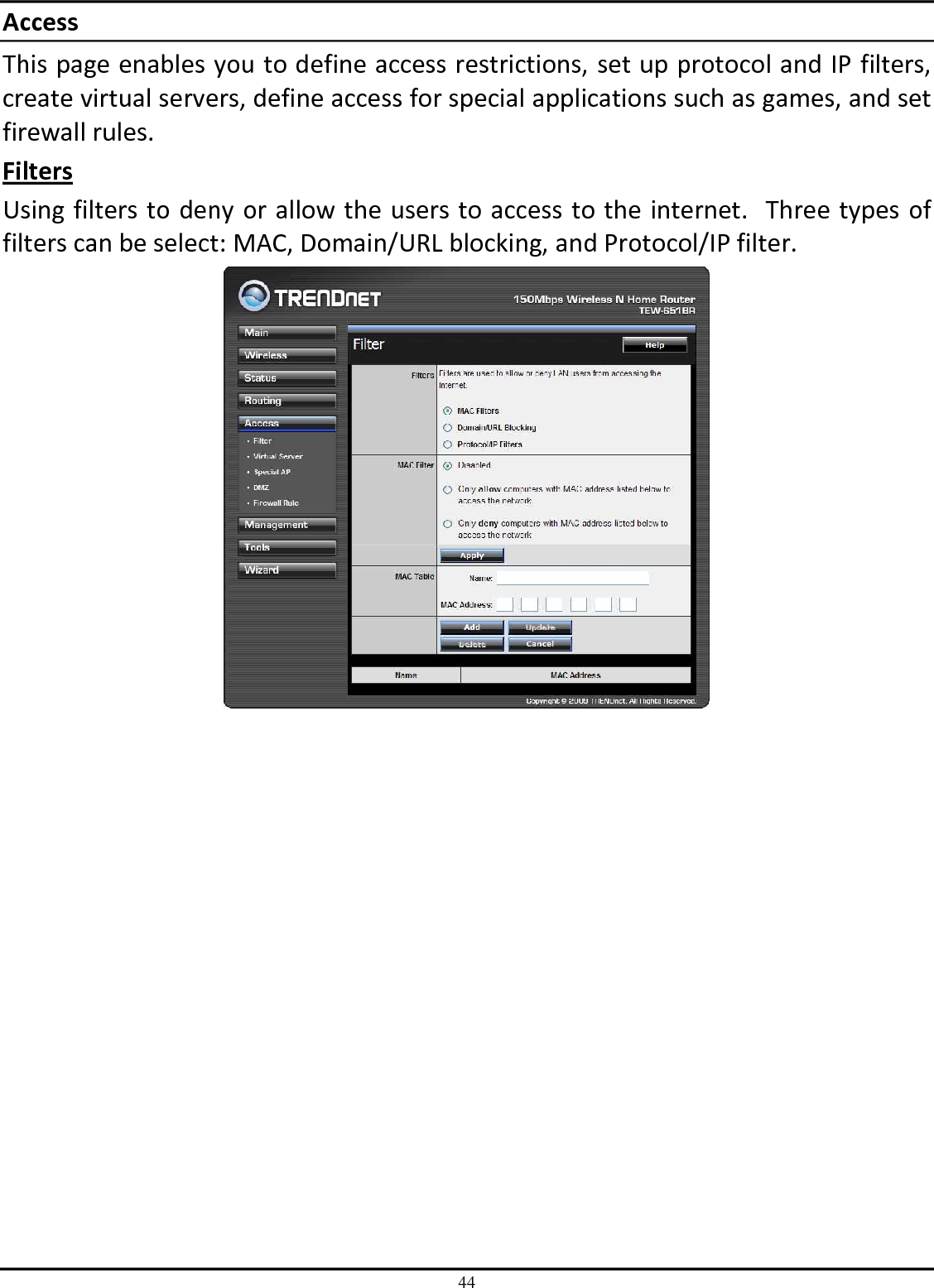
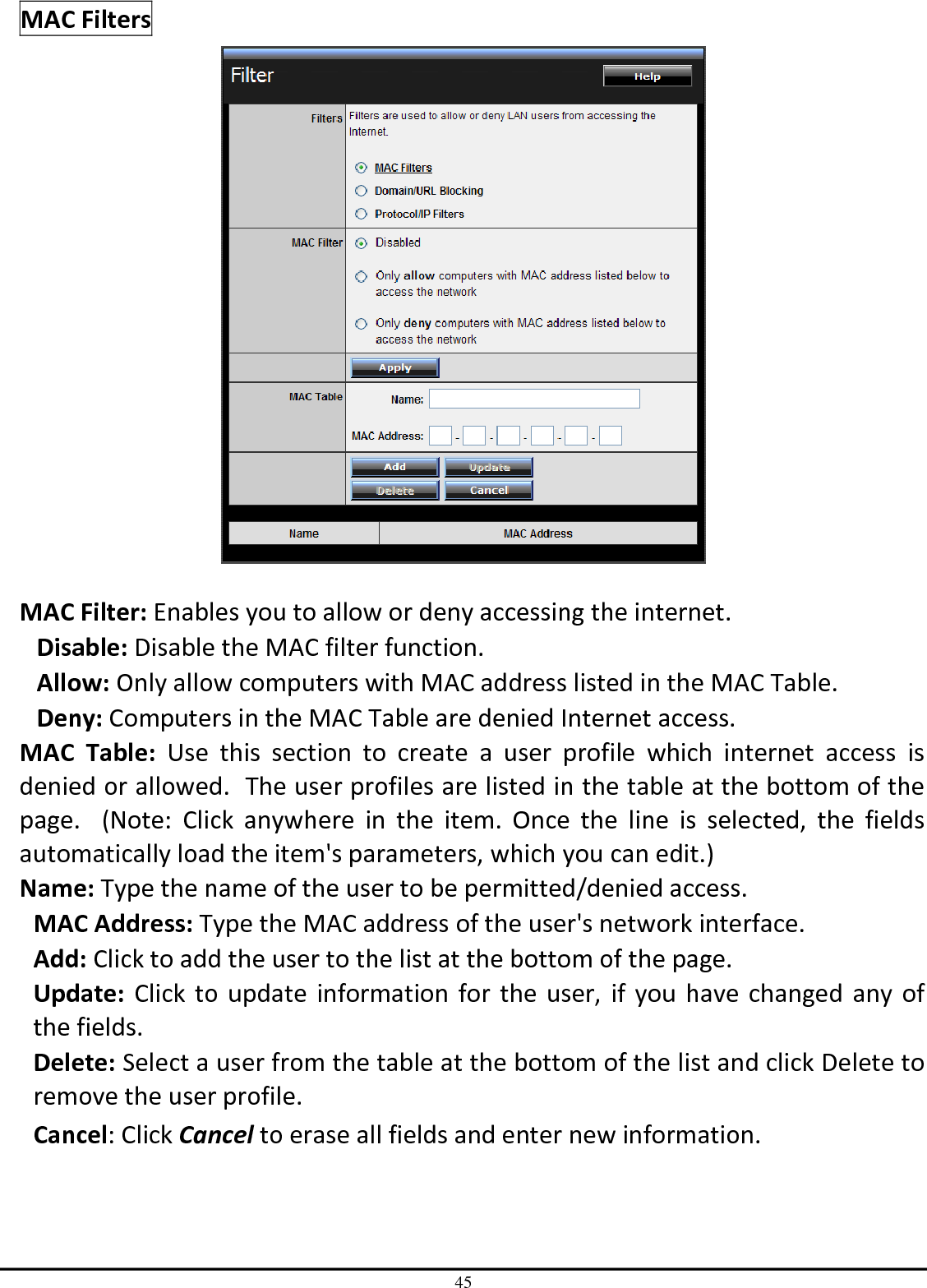
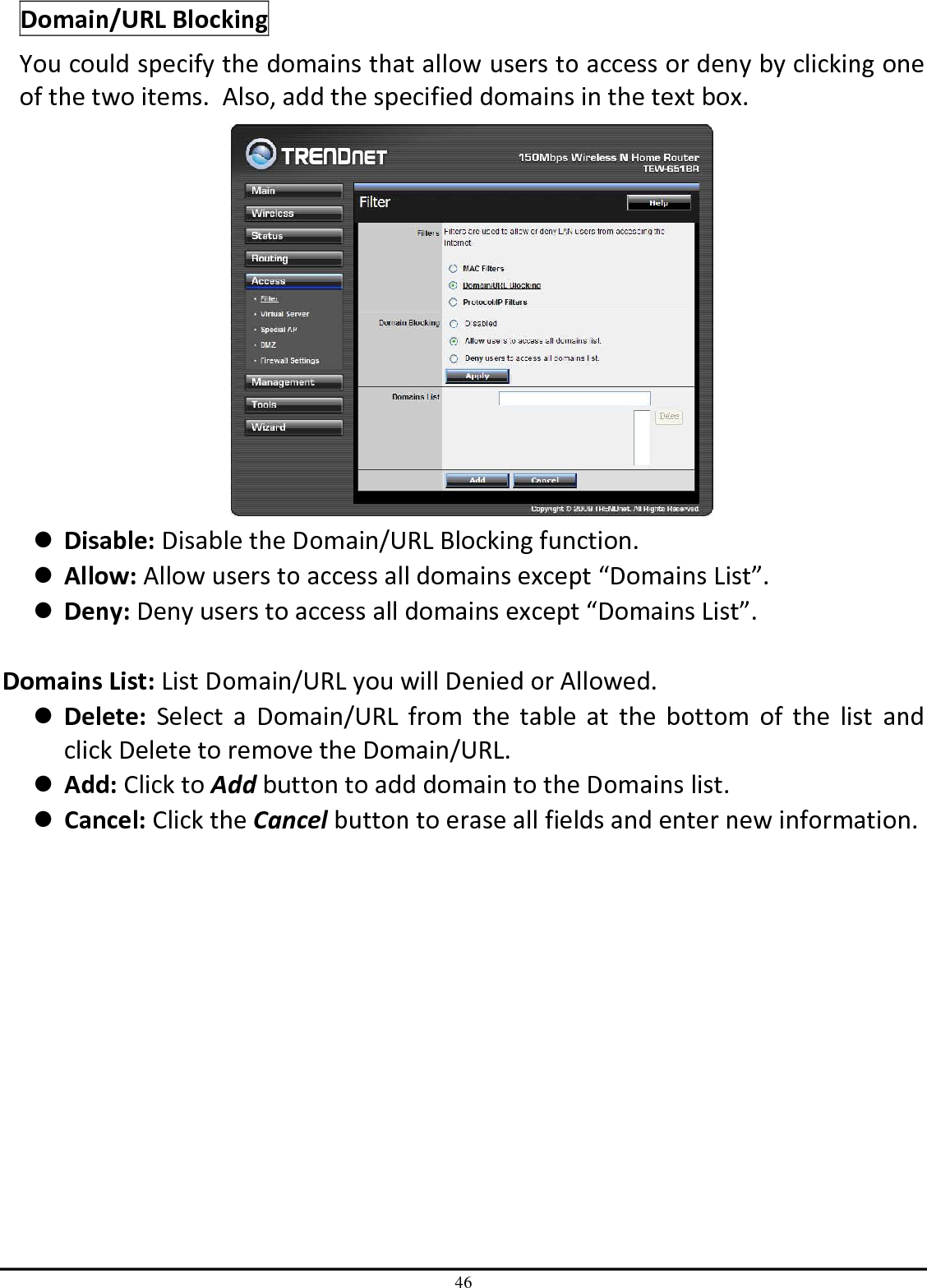
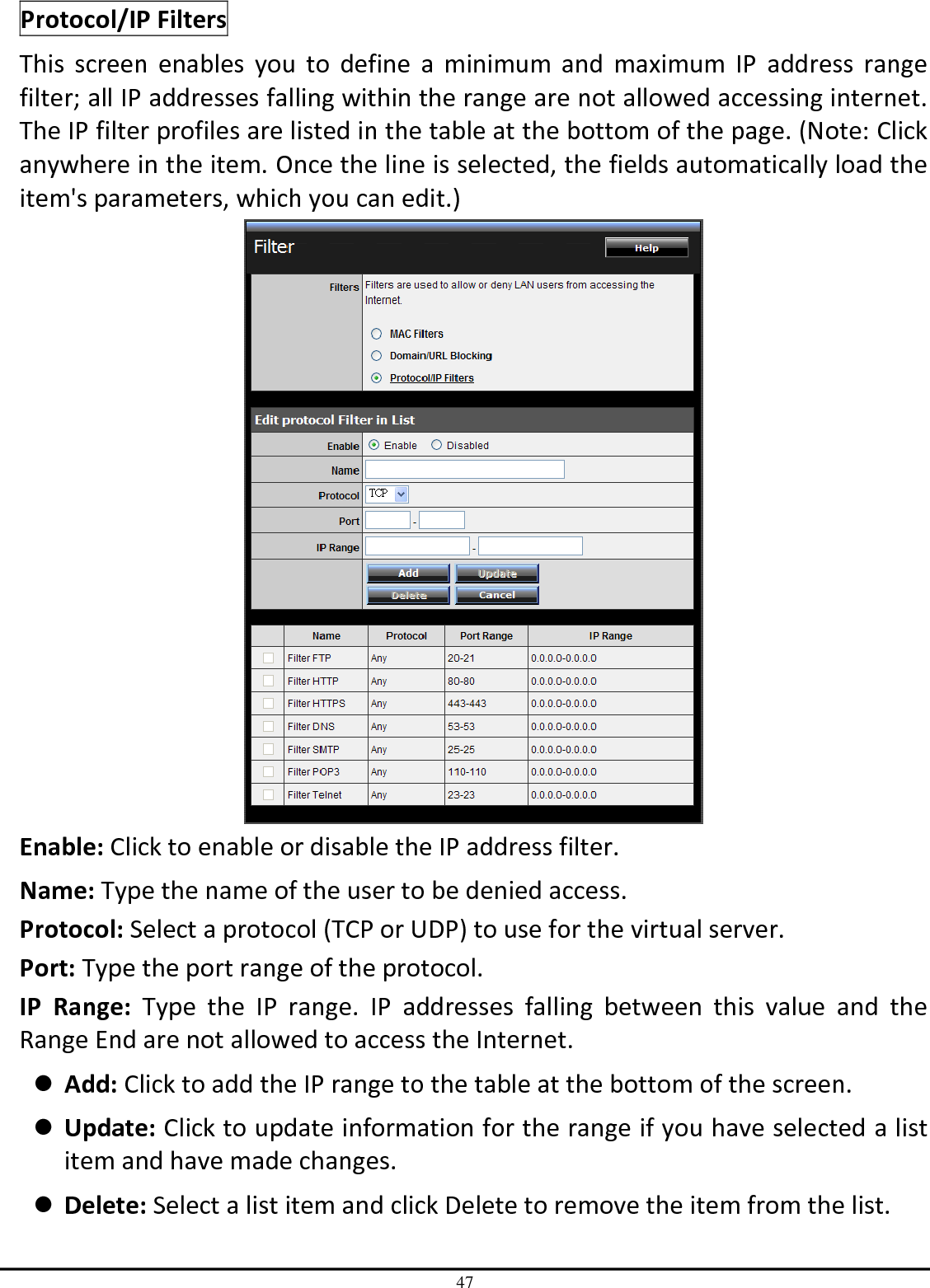
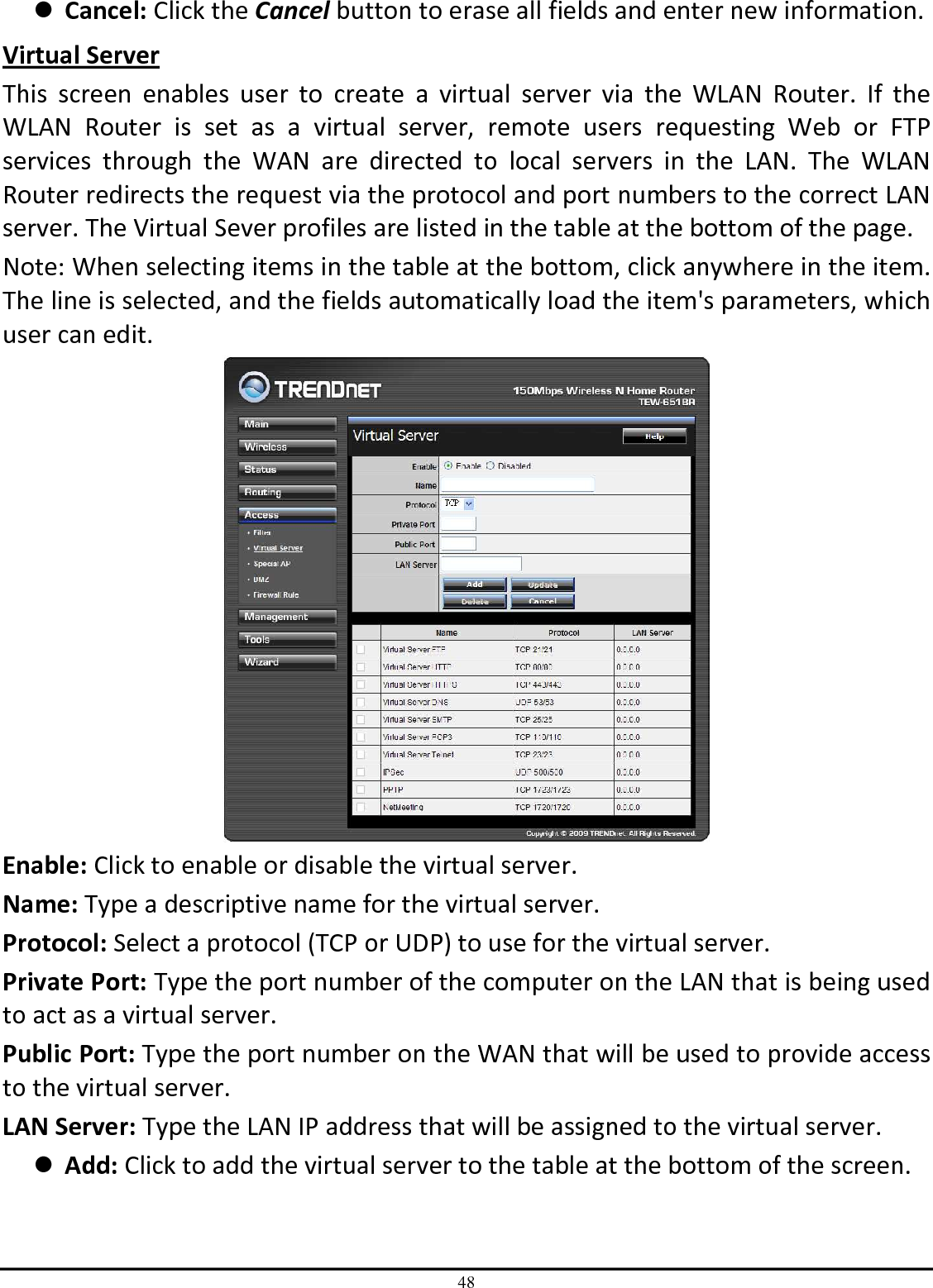
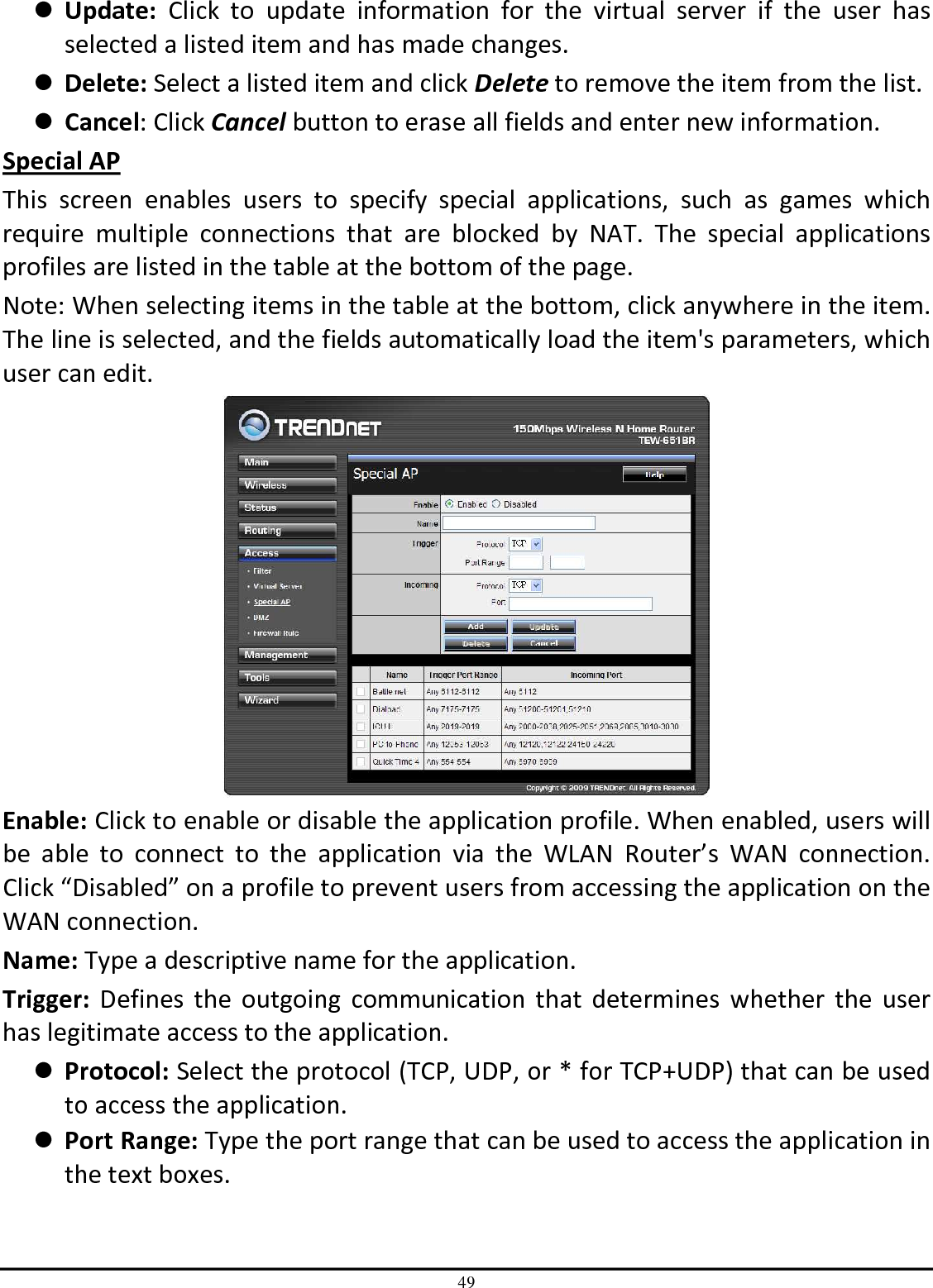
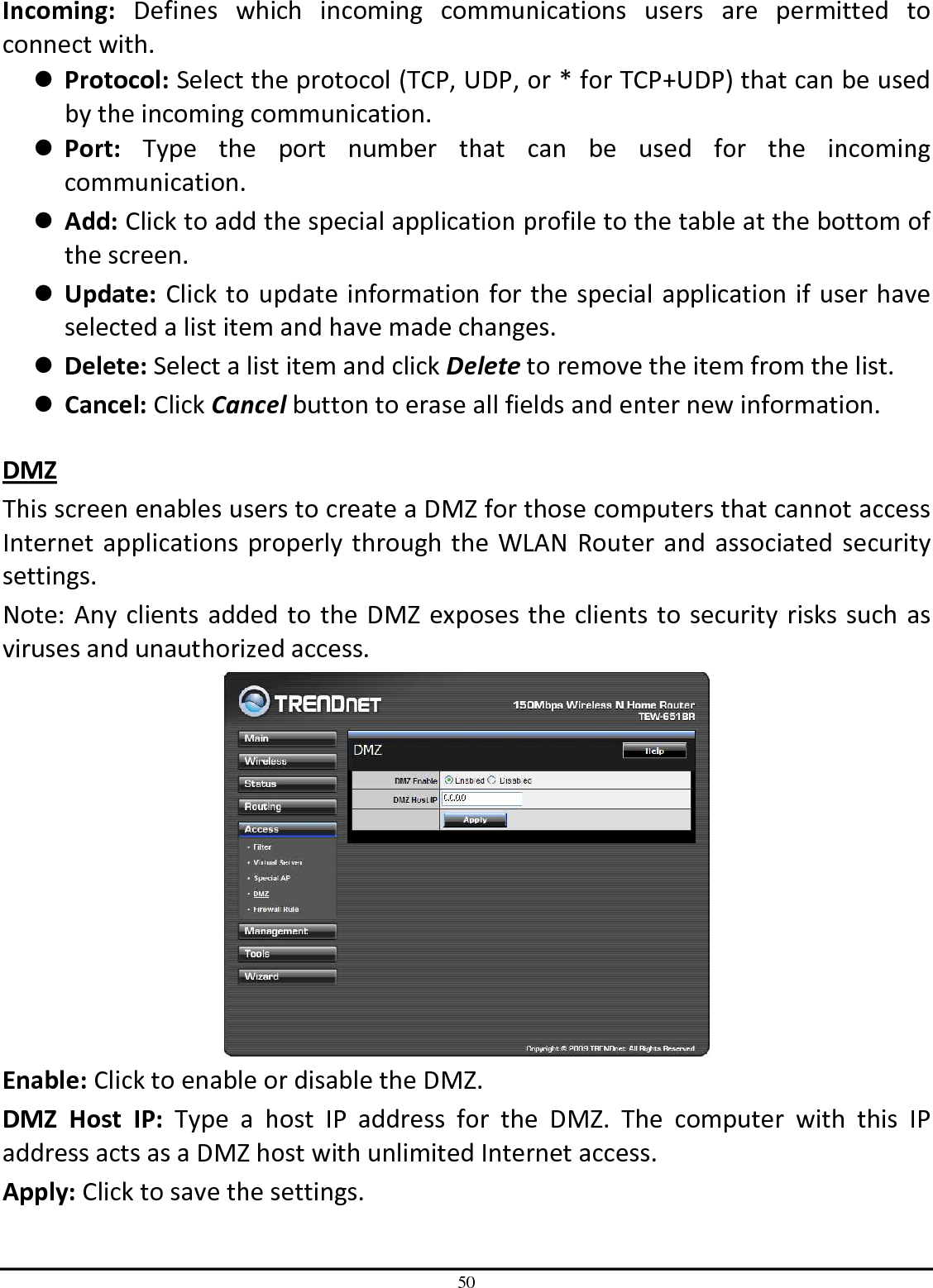
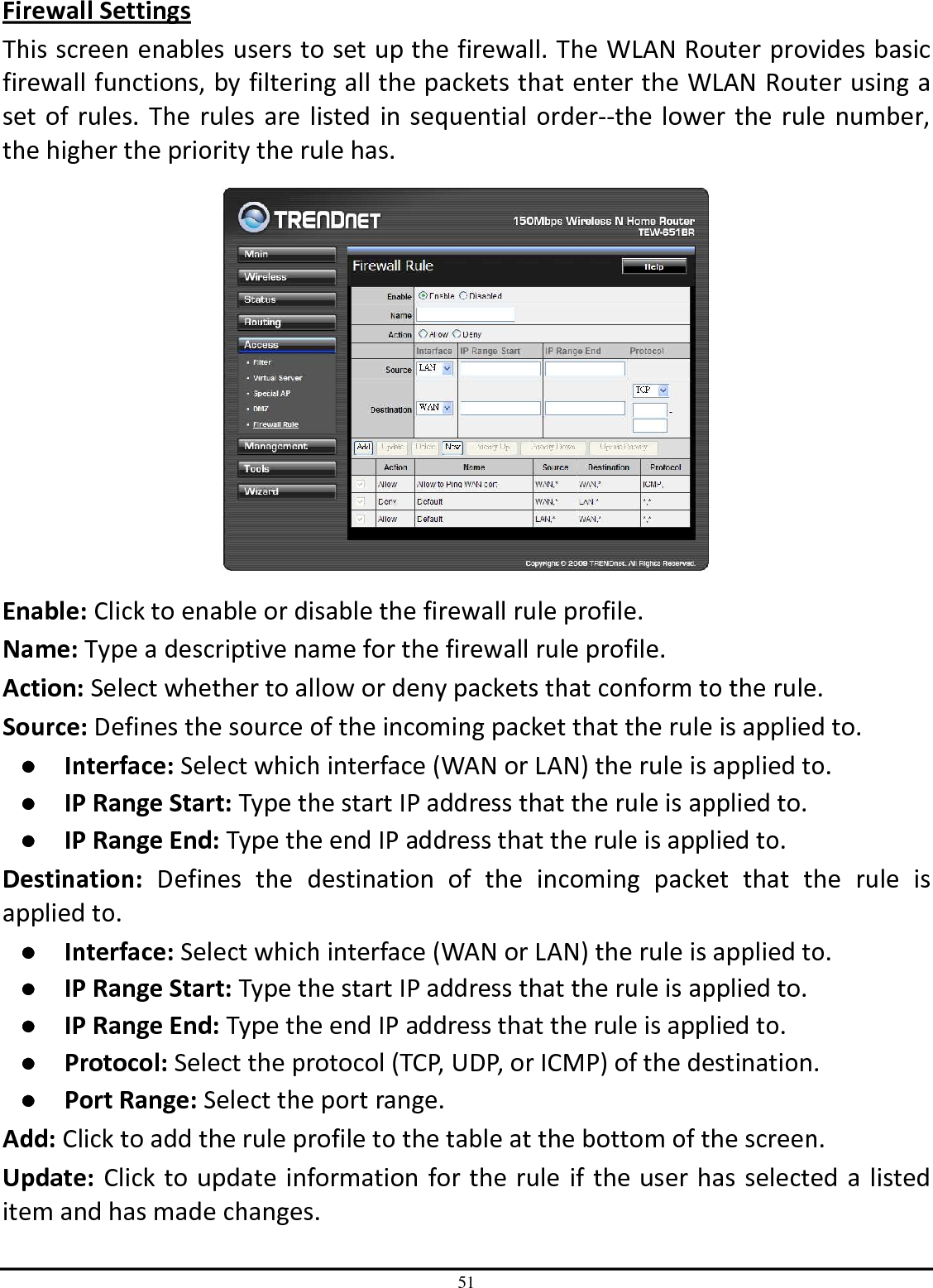
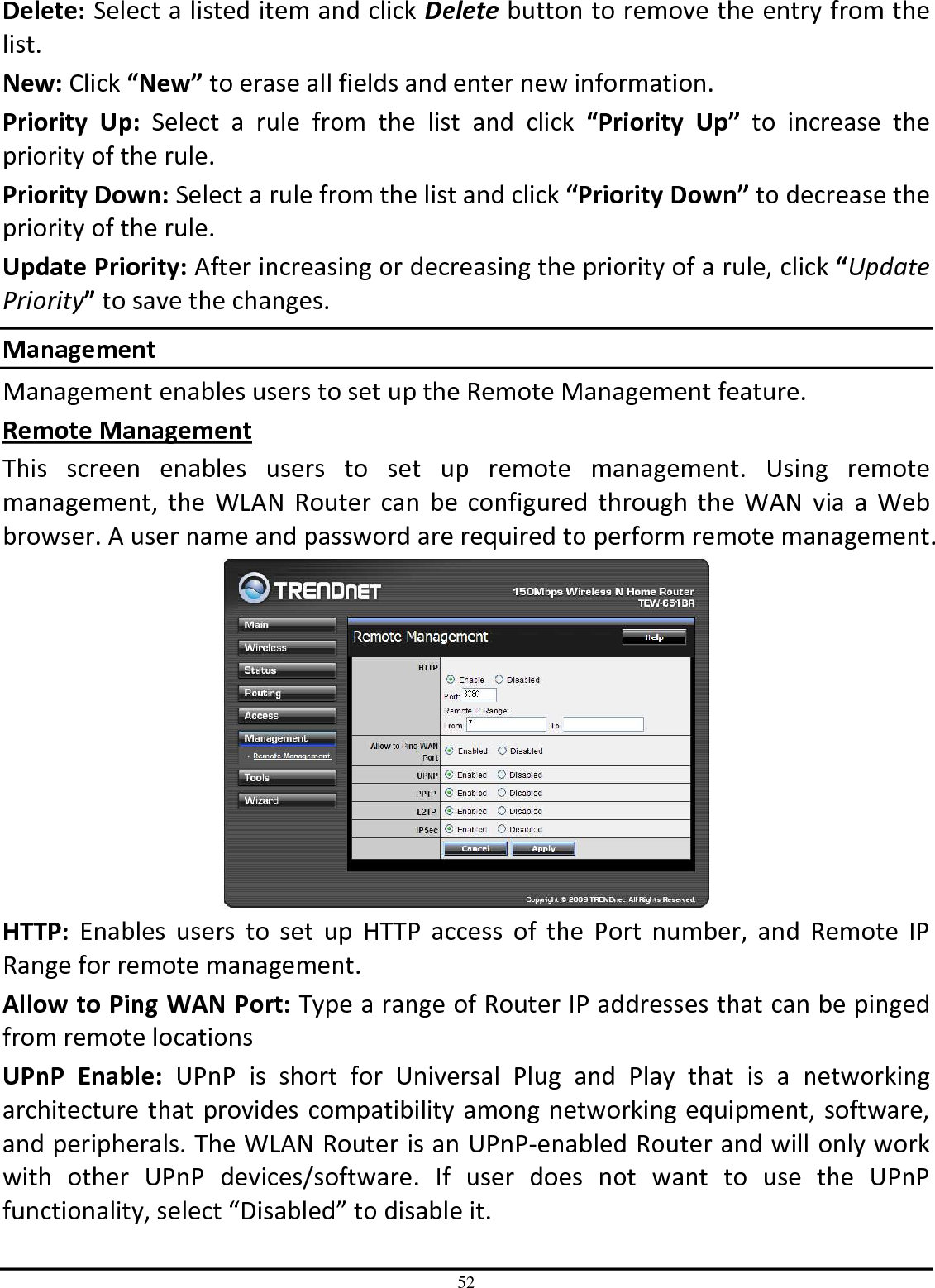
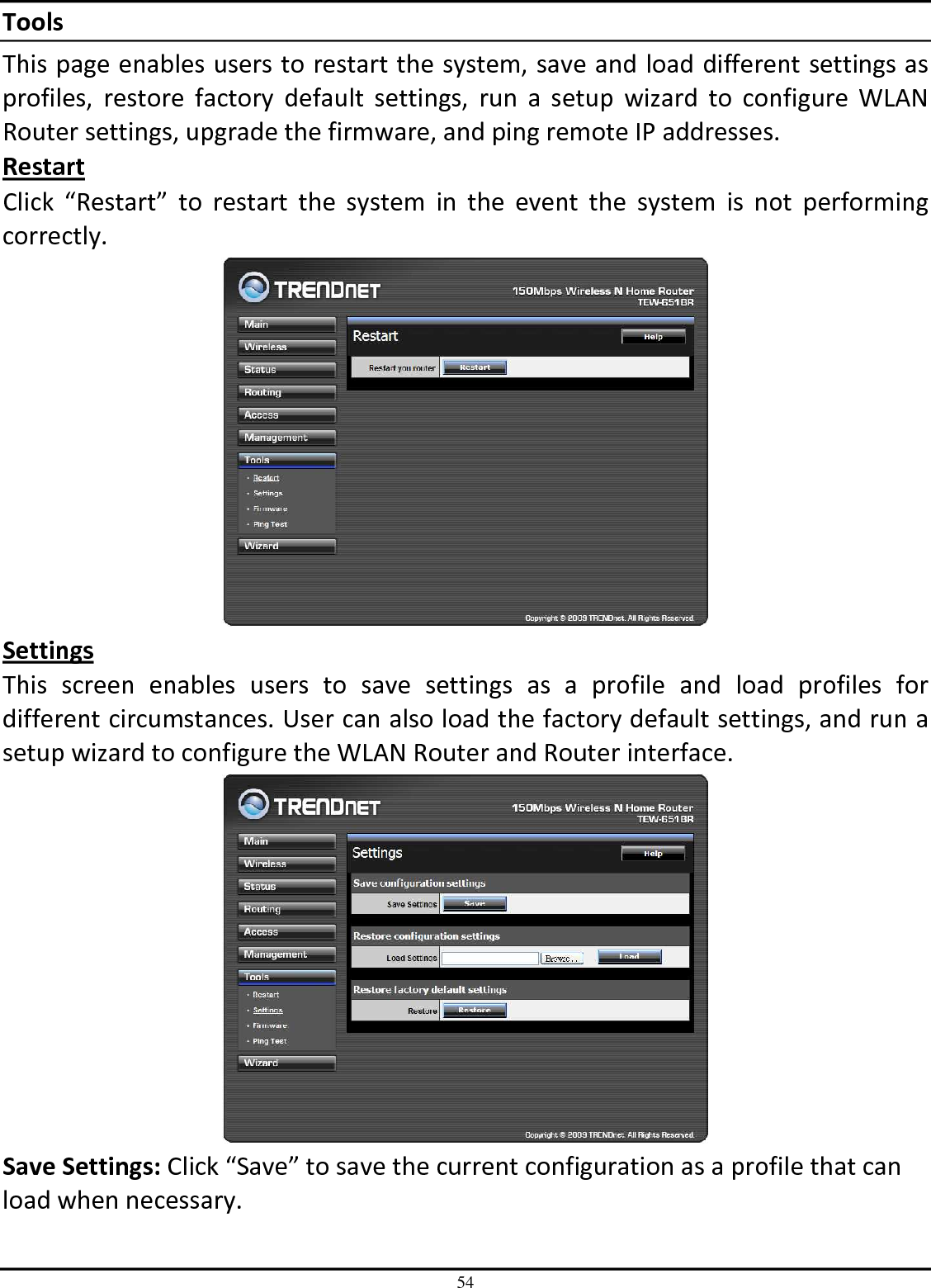
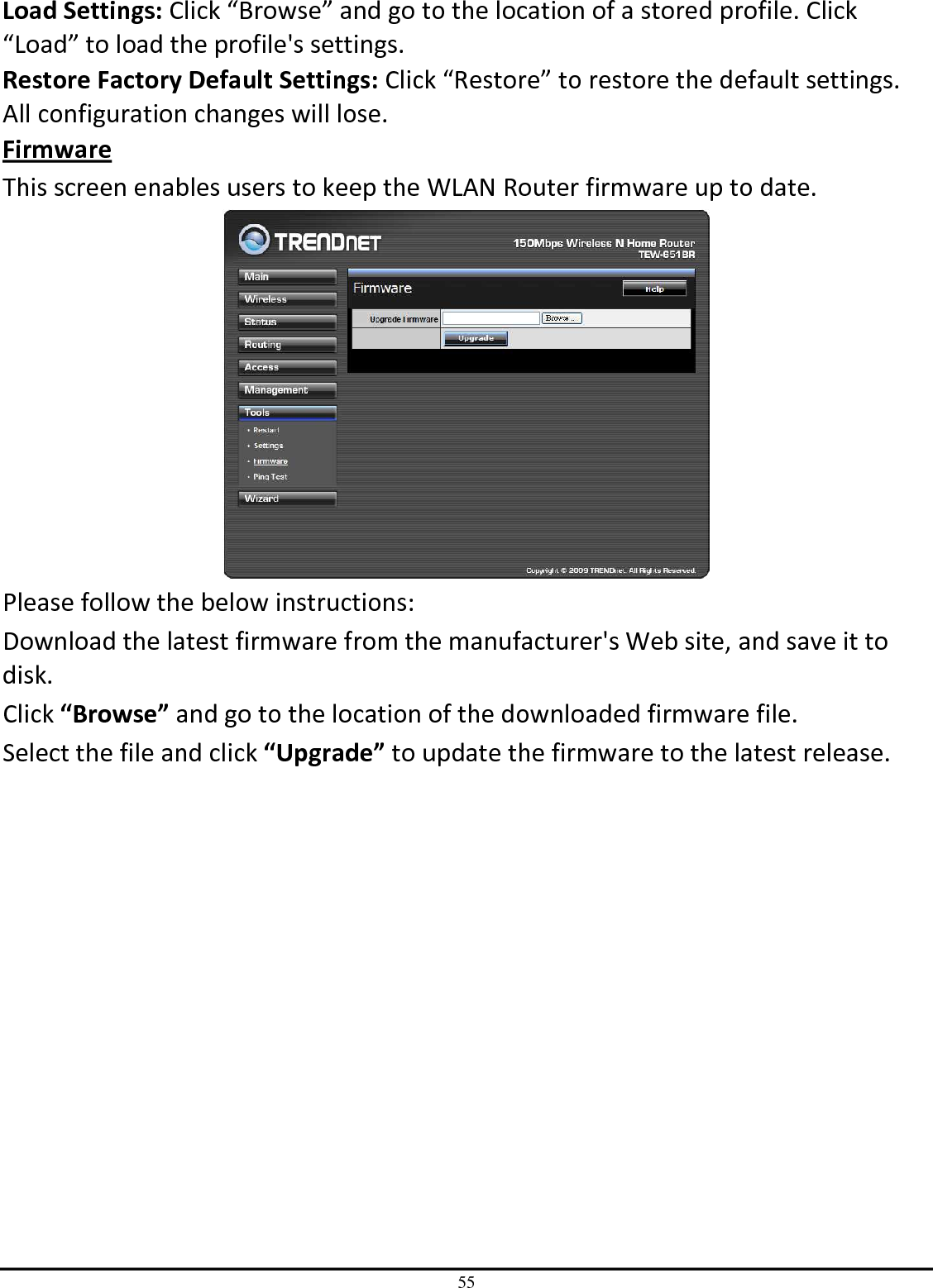
TRENDNET TEW651BR 150Mbps Wireless N Home Router User Manual UG TEW 651BR 1 02
TRENDNET, Inc. 150Mbps Wireless N Home Router UG TEW 651BR 1 02
TRENDNET >
Contents
- 1. UserMan-1_XU8TEW651BR
- 2. UserMan-2_XU8TEW651BR
UserMan-2_XU8TEW651BR