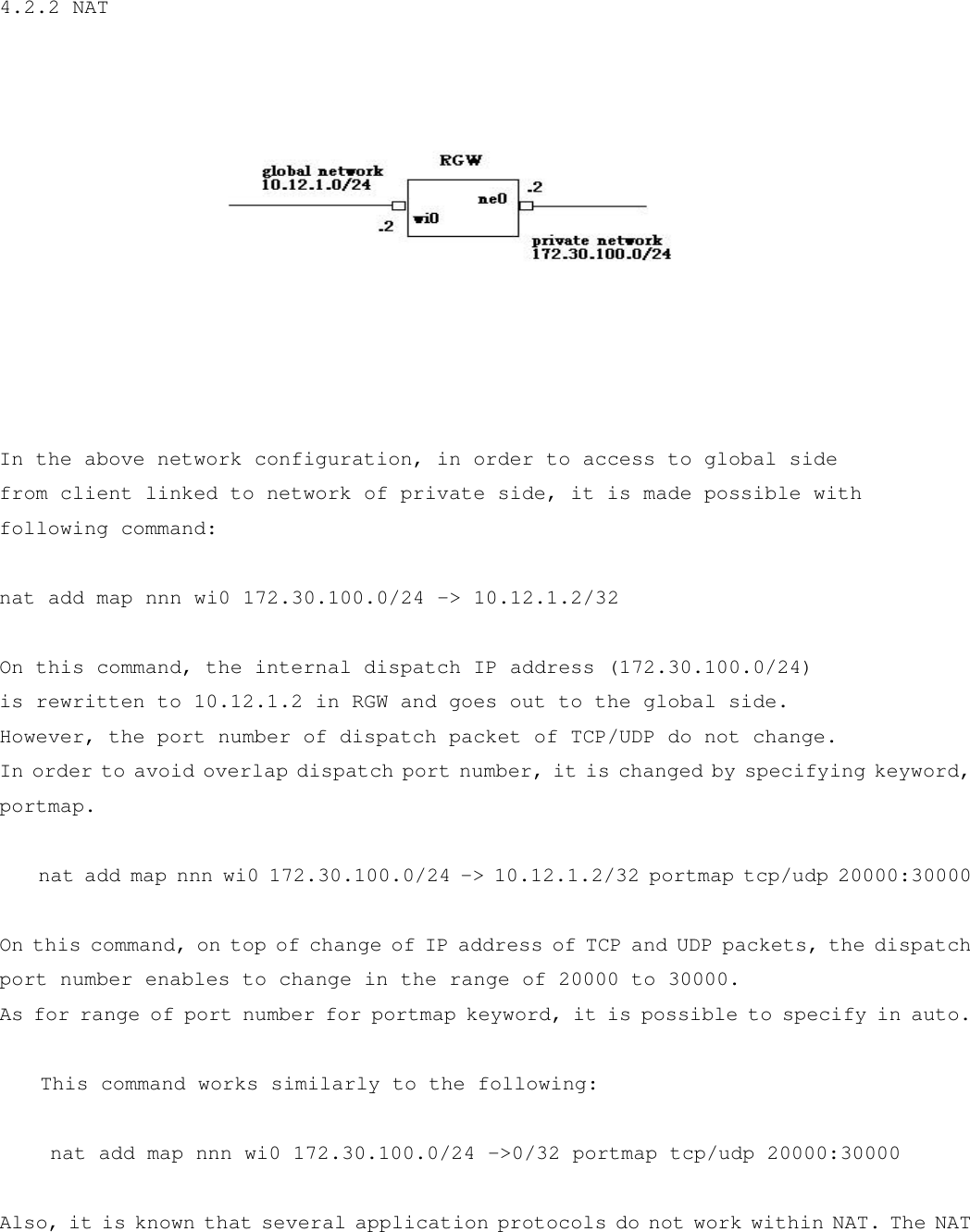
Root RGW2400-OD Direct Sequence Spread Spectrum Transceiver User Manual 1 4 1E 2 1 Wiya comments
Root Inc Direct Sequence Spread Spectrum Transceiver 1 4 1E 2 1 Wiya comments
Root >
Contents
- 1. User Manual
- 2. Program manual
- 3. US power limitation
Program manual

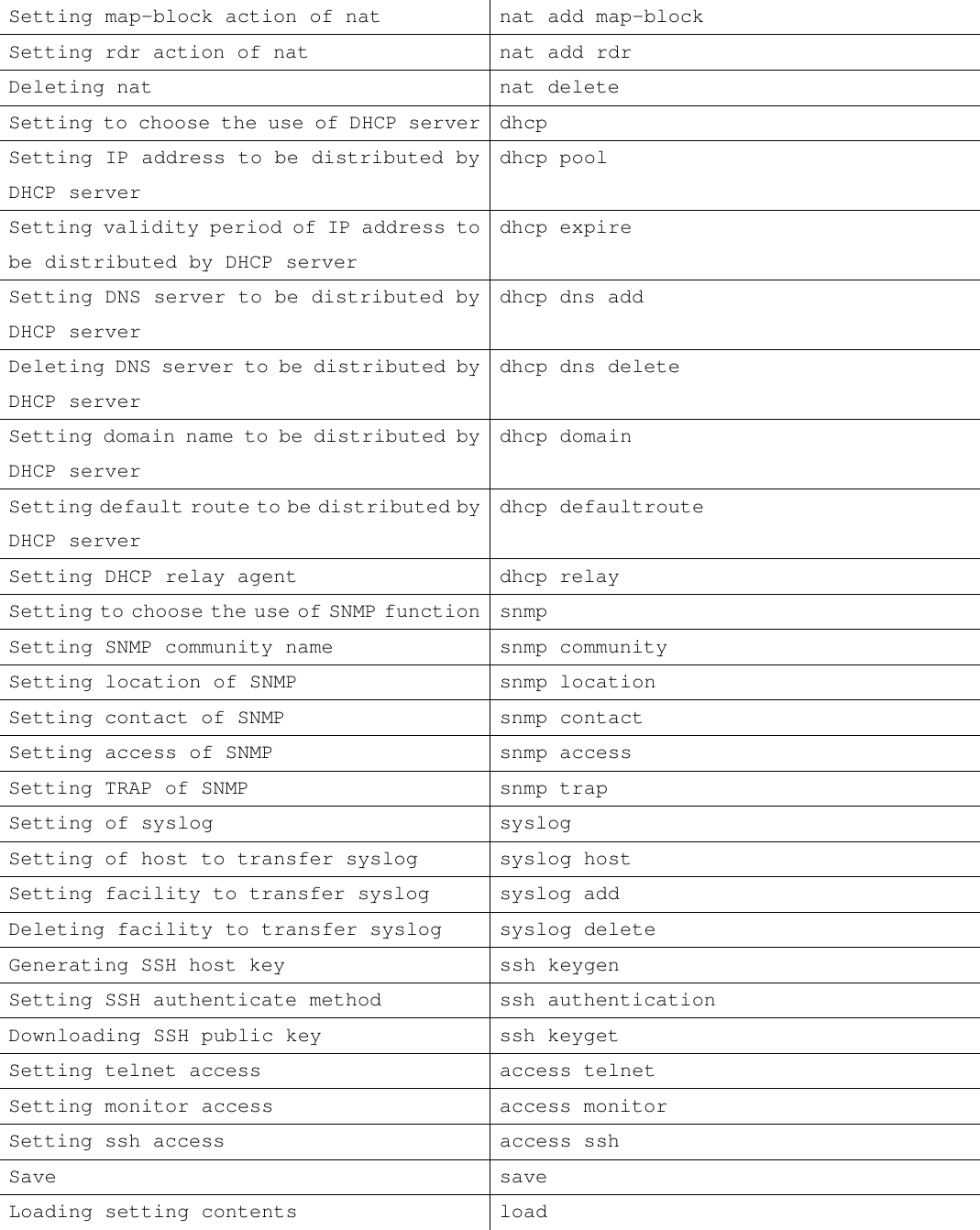
![1.4.1 List of Command Line Shell Functions Function Description Supplement to Command By pressing [TAB] key, command string is inserted to the supplemental part possible Help on Commands By pressing [?] key, displays list of available command or description of each command. Example: $ip? *ip address *ip route add *ip route delete Since no command is formed in ip, commands starting with ip are displayed. $ ip address ? usage: ip address"Interface Ipaddress Netmask" e.g. : $ ip address ep0 192.168.0.100 255.255.255.0 Since the command "ip address" is unique, usage and examples are displayed. Editing Command Line This function supports editing of command line. The key bind of each is as follows: Key Description Back Space Deletes one character before cursor Ctrl-A Moves cursor to the head of command line Ctrl-E Moves cursor to the end of command line Ctrl-D Deletes the character on cursor Ctrl-U Deletes the entire command line Ctrl-F (->) Moves cursor to the right Ctrl-B (<-) Moves cursor to the left Ctrl-K Deletes the character after cursor Record of Entered Commands Retains records of inputted command Key Description Ctrl-P Calls previous recorded entry Ctrl-N Calls next recorded entry](https://usermanual.wiki/Root/RGW2400-OD.Program-manual/User-Guide-258965-Page-4.png)
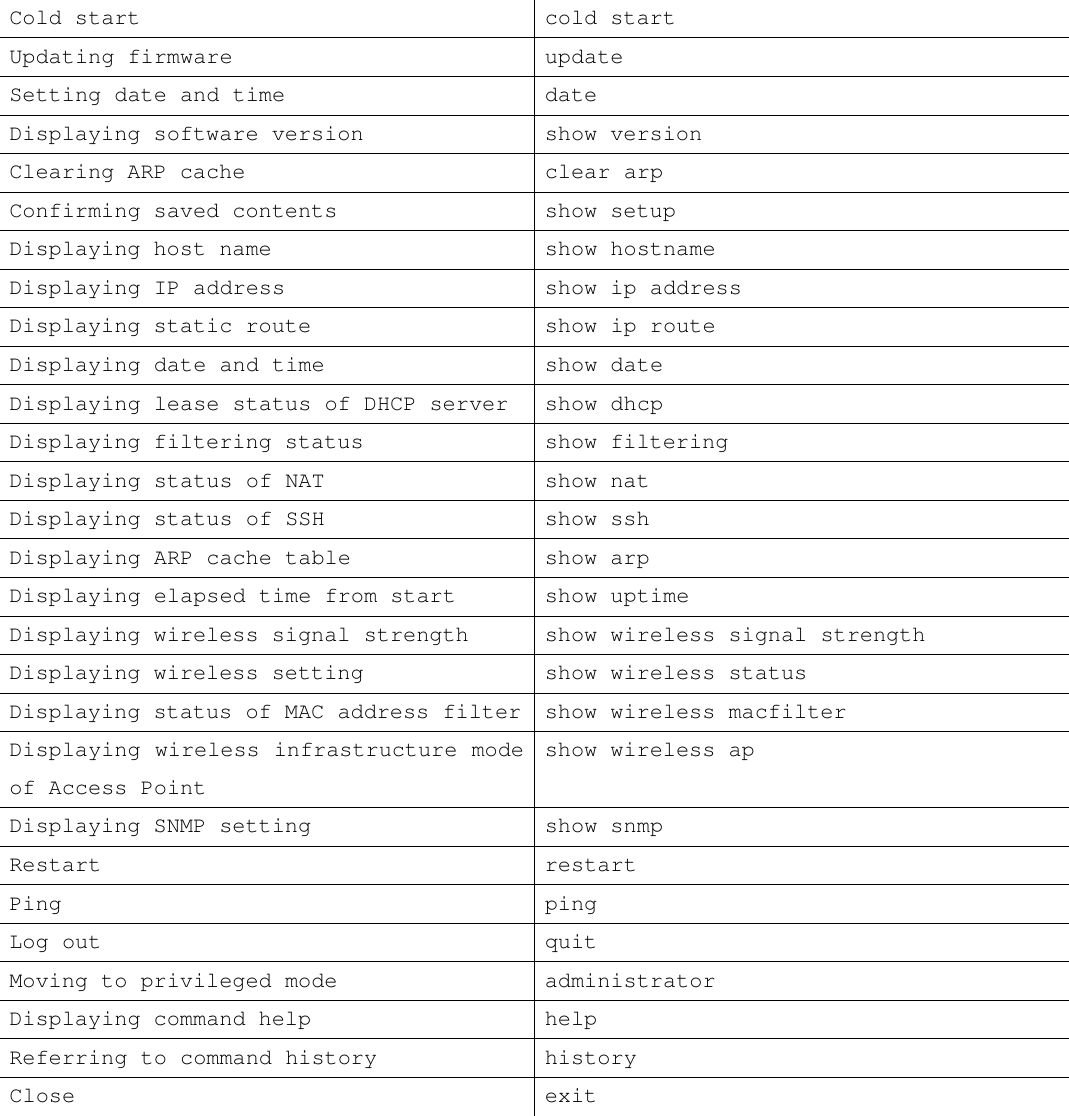
![1.6 Typographical Conventions Typographical conventions used in the command list are shown below. Convention Description Example(s) Courier new, regular style Command ip address italics Indicates a variable which must be replaced with a real value. ip address Interface IPaddress Netmask square brackets [ ] The argument within the brackets may be omitted. Do not enter the brackets in the command line. ssh keygen version [overwrite] Quotation marks " " Enclosed expression must be entered exactly as shown (hard coded). Do not enter the quotation marks in the command line. "all" | bar (exclusive OR) You must enter one, and only one, of the items separated by the bar. Do not enter the bar in the command line. ne0| wi0| lo0 Braces { } List of arguments from which you must choose an item in syntax descriptions, or an enclosed phrase. Do not enter the braces in the command line. Port { = | ! | <= | >= } portNo](https://usermanual.wiki/Root/RGW2400-OD.Program-manual/User-Guide-258965-Page-8.png)
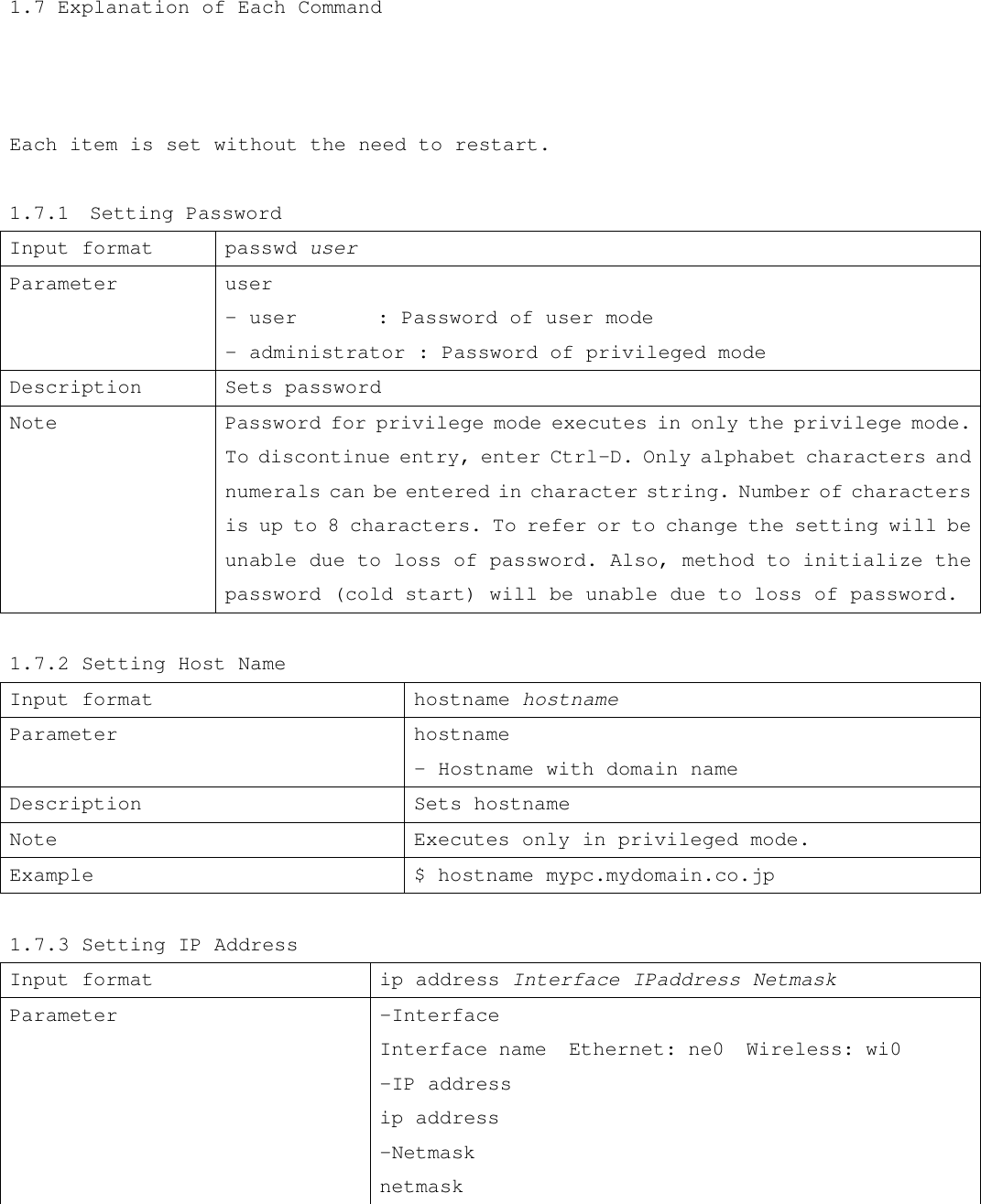
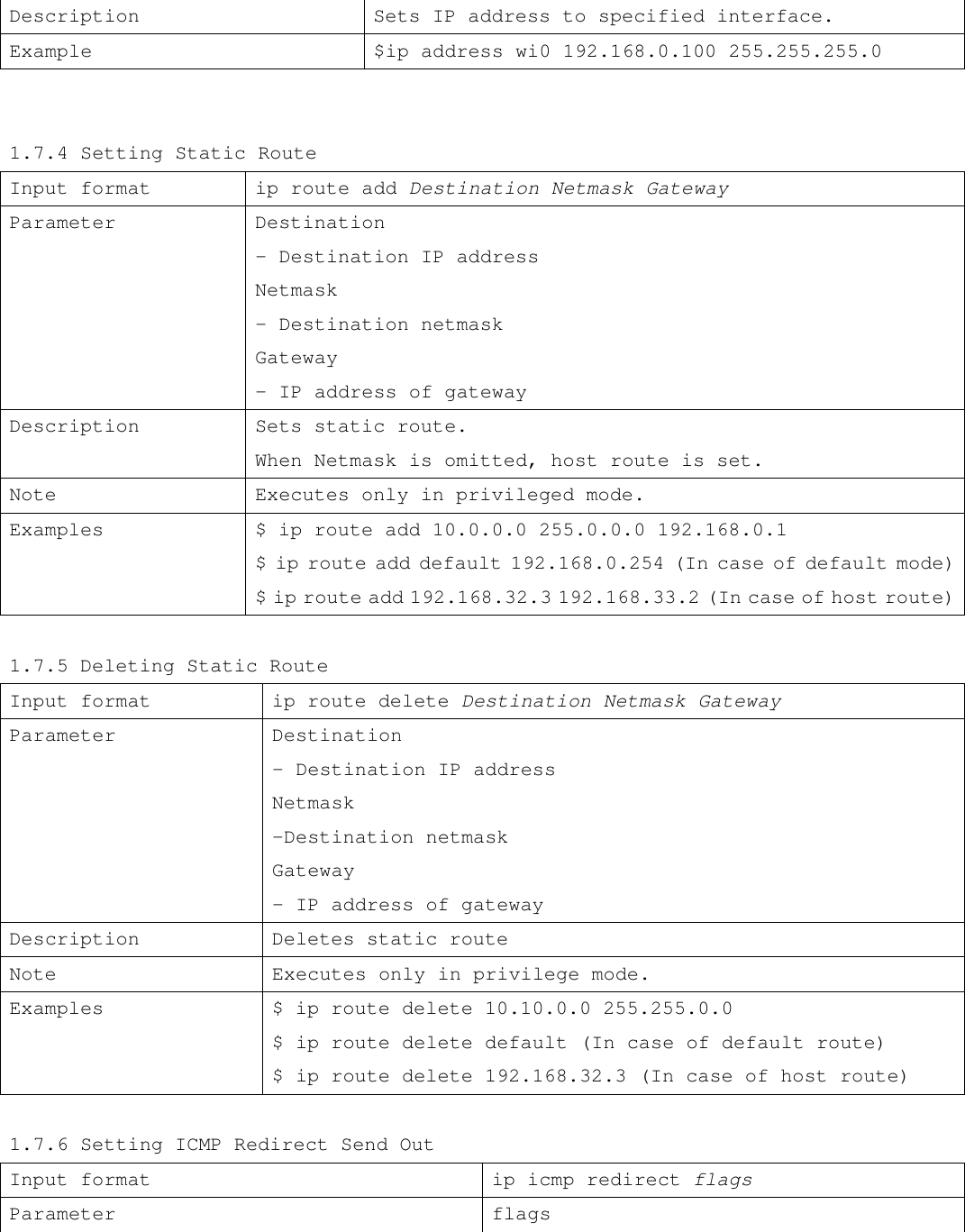
![Example $ wireless network NetBSD_IBSS 1.7.14 Setting Wireless Station Input format wireless station value Parameter Value - Station name of BSS mode (max. 30 characters) Description Sets station name during BSS mode Notes Executes only in privileged mode. Sets a distinguishing name and is valid in wireless port 1 during BSS mode. Some monitoring programs poll the station name of each wireless client in the BSS for identification purposes. Example $ wireless station NetBSD_Wave LAN/IEEE_node 1.7.15 Switching to Wireless Infrastructure Mode of Access Point Input format wireless BSS AP mode flag Parameter flag - enable: Set infrastructure mode of Access Point - disable: Delete infrastructure mode of Access Point Description Sets RGW to function as the Access Point in an 802.11b BSS. Notes Executes only in privileged mode. Access Point is enabled [disabled] after the following commands are entered: 1. wireless BSS AP mode enable [disable] 2. save 3. restart 4. save When flag is set to disable, RGW operates in ad-hoc mode. Important note: The SSID cannot be modified after wireless BSS AP mode is enabled. SSID parameter should be set using wireless ssid command (section 1.7.16) prior to enabling wireless BSS AP mode. Example $ wireless BSS AP mode enable 1.7.16 Setting Wireless SSID](https://usermanual.wiki/Root/RGW2400-OD.Program-manual/User-Guide-258965-Page-14.png)
![- disable : Neither send nor receive route Description Sets RIP action Note Executes only in privileged mode. Example rip action wi0 supply 1.7.22 Setting RIP Version Input format rip version interface version Parameter interface -interface name version - ripv2:Uses RIPv2 (multicast) - ripv12:Uses RIPv2 (multicast ) and RIPv1 (broadcast). - ripv1:Uses RIPv1 (broadcast). Description Sets RIP version. Notes Executes only in privileged mode. Example $ rip version wi0 ripv2 1.7.23 Setting to Use Filter Input format Filter flag Parameter flag - enable : In use - disable : Not in use Description Chooses to use IP filter or not Note Executes only in privileged mode. Example $ filter enable 1.7.24 Setting IP Filter Input format filter add number action inout [ log level facility.level][quick] [on interface] [proto proto] [ from [!] address [port] to [!] address [port] ] [flags] [with] [keep] [group] Parameter number -0-655335 : Filter No. action](https://usermanual.wiki/Root/RGW2400-OD.Program-manual/User-Guide-258965-Page-17.png)

![- group N : sets rule in group N Description Sets filtering for IP packet Note Executes only in privileged mode. Sorted according to filter No. and set in ascending order. Example $ filter add 100 block out proto tcp from 100.100.0.0/16 to any port = 80 1.7.25 Deleting IP Filter Input format filter delete number Parameter number - 0-65535 : filter No. Description Deletes filtering for IP packet Note Executes only in privileged mode. Example $ filter delete 100 1.7.26 Setting the Use of NAT Input format nat flag Parameter flag - enable : Use - disable : No use Description Chooses use or no use of NAT. Note Executes only in privileged mode. NAT function in Ethernet side will be valid when switched to enable , factory set (wireless side: global and Ethernet side: private). Example $ nat enable 1.7.27 Setting map Action of NAT Input format nat add map number interface address1 -> address2 [portmap Proto ports| proxy port portname tag/protocol] Parameter Number - 0-255 : NAT No. (common at nat add * command) interface - name of interface address1](https://usermanual.wiki/Root/RGW2400-OD.Program-manual/User-Guide-258965-Page-19.png)
![Description Sets bimap action of NAT Notes Executes only in privileged mode. Sorted according to nat No. common to nat setup and set in ascending order. Example $ nat add bimap 3 ne 10.0.0.5/32 -> 210.100.100.101/32 1.7.29 Setting map-block Action of NAT Input format nat add map-block number interface address1 -> address2 [ports port] Parameter number - 0-255 : NAT No.(common at nat add*command) interface - name of interface address1 - IP address on local side - 1.2.3.4/xx format adderss2 - IP address on global side - 1.2.3.4/xx format port - auto|port No. Description Sets mapblock action of NAT Note Executes only in privileged mode. Sorted according to nat No. common to nat setup and set in ascending order. Example $ nat add map-block 2 ne 10.0.0.5/8 -> 210.100.100.101/24 ports auto](https://usermanual.wiki/Root/RGW2400-OD.Program-manual/User-Guide-258965-Page-21.png)
![Input format nat flag [interface] Parameter flag - enable : Use - disable : Not in Use interface - name of interface using DHCP server function. It assumes ne0 when omitted. Not required during disable. Description Chooses between use and no use of DHCP server function. Notes Executes only in privileged mode. Distribute IP address must be in the interface network. Refer to limitation for details. Example $ dhcp enable 1.7.33 Setting IP Address Range to be Distributed through DHCP server Input format dhcp pool ipaddress1 ipaddress2 Parameter ipaddress 1 - Head of IP address ipaddress2 - End of IP address Description Sets range of IP address to be distributed through DHCP server. Note Executes only in privileged mode. Example $ dhcp pool 192.168.0.1 192.168.0.254 1.7.34 Setting Expiration of IP Address to be distributed through DHCP server Input format dhcp expire period Parameter period - Expiration of IP address (Second) Description Sets expiration of IP address to be distributed through DHCP server. Note Executes only in privileged mode. Example $ dhcp expire 7200](https://usermanual.wiki/Root/RGW2400-OD.Program-manual/User-Guide-258965-Page-23.png)
![1.7.35 Setting DNS Server to be distributed through DHCP server Input format dhcp dns add ipaddress Parameter ipaddress * IP address of DNS server Description Sets DNS server to be distributed through DHCP server. Note Executes only in privileged mode. Maximum of 2 can be registered. Example $ dhcp dns add 210.100.100.101 1.7.36 Deleting DNS Server to be distributed through DHCP server Input format dhcp dns delete ipaddress Parameter ip address -iP address of DNS server Description Deletes DNS server to be distributed through DHCP server. Note Executes only in privileged mode. Example $ dhcp dns delete 210.100.100.101 1.7.37 Setting Domain Name to be distributed through DHCP server Input format dhcp domain domainname Parameter domainname - Domain name Description Sets domain name to be distributed through DHCP server. When domainname is omitted, domain name is not distributed. Note Executes only in privileged mode. Example $ dhcp domain root-hq.com 1.7.38 Setting Default Route to be distributed through DHCP server Input format dhcp defaultroute [defaultroute] Parameter defaultroute -IP address of default route Description Sets default route to be distributed through DHCP server. When defaultroute is omitted, default route is not distributed. Note Executes only in privileged mode. Example $ dhcp defaultroute 172.30.100.2](https://usermanual.wiki/Root/RGW2400-OD.Program-manual/User-Guide-258965-Page-24.png)
![Example $ snmp location 1-17-8 Nishikata Bunkyo-ku Tokyo Japan 1.7.43 Setting Contact of SNMP Input format snmp contact str Parameter str - Character string Description Sets contact of SNMP. Up To maximum of 255 characters. Note Executes only in privileged mode. Example $ snmp contact Tarou Yamada <taro@root-hq.com> 1.7.44 Setting Access of SNMP Input format snmp access [ipaddress|network] Parameter ipaddress -ip address | "all" network -network address with netmask 255.255.255.0 format Description Specifies accessible host range to RGW with SNMP . Notes Executes only in privileged mode. Checking of IP filter is implemented prior to checking the setting of this access. Example $ snmp access 192.168.0.0 255.255.255.0 1.7.45 Setting SNMP TRAP Input format snmp trap mode flag [community [port]] Parameter mode - v1|v2|inform v1:snmp v1 v2:snmp v2 inform:NOTIFICATION flag](https://usermanual.wiki/Root/RGW2400-OD.Program-manual/User-Guide-258965-Page-26.png)
![Parameter facility kern | user | auth | authpriv | syslog | cron | ftp | uucp | local0-7 | daemon |* level emerg | alert | crit | err | warning | notice | info | debug | none | * Description Sets facility and its level to transfer syslog. Note Executes only in privileged mode. Example $ syslog add * info 1.7.49 Deleting Facility to Transfer syslog Input format syslog delete facility level Parameter facility kern | user | auth authpriv| syslog | cron | ftp | uucp | local0-7| daemon |* level emerg | alert | crit | err | warning | notice | info | debug | none | * Description Sets facility and its level to delete syslog. Note Executes only in privileged mode. Example $ syslog delete kern crit 1.7.50 Generating Host Key of SSH Input format ssh keygen version [overwriteßIsn’t it better to enclose it with “ “? because it is hard coding] Parameter version - v1 : generate host key of SSHv1 - v2 : generate host key of SSHv2 - v12 : generate host key of both SSHv1 and SSHv2](https://usermanual.wiki/Root/RGW2400-OD.Program-manual/User-Guide-258965-Page-28.png)
![Example $ ssh keyget v1 http://192.168.0.12/~rgw/identity.pub 1.7.53 Switching Version of SSH Input format ssh version version Parameter version - v1: SSHv1 - v2: SSHv2 - v12: both Description Switches Version of SSH Notes An access will be valid with specified SSH version by this command. Executes only in privileged mode. Ver 1.4.0 and later only can be used on this command. Example $ ssh version v12 1.7.54 Setting telnet Access Input format access telnet [ipaddress|network] Parameter ipaddress - IP address | "all" network - network address having netmask 255.255.255.0 format Description Specifies host range possible to access to RGW with telnet. Notes Executes only in privileged mode. Checking IP filter is implemented prior to checking setup access Example 1.7.55 Setting http Access Input format access http [ipaddress|network] Parameter Description Notes Example éThis command explanation is missing. 1.7.56 Setting monitor Access](https://usermanual.wiki/Root/RGW2400-OD.Program-manual/User-Guide-258965-Page-30.png)
![Input format access monitor [ipaddress|network] Parameter ipaddress - IP address | "all" network - network address having netmask 255.255.255.0 format Description Specifies host range possible to access to RGW with monitor. Notes Executes only in privileged mode. Checking IP filter is implemented prior to checking setup access. The monitor is an application which displays wireless condition of RGW that operates on Windows. It can be downloaded from ROOT Inc. home page. Example 1.7.57 Setting SSH Access Input format access ssh [ipaddress|network] Parameter ipaddress - IP address | "all" network - network address having netmask 255.255.255.0 format Description Specifies host range possible to access to RGW with ssh. Notes Executes only in privileged mode. Checking IP filter is implemented prior to checking setup access. Example 1.7.58 Save Input format save Parameter None Description Saves setup contents. Notes Executes only in privileged mode. Reflected on system file and setup file is saved in command format.](https://usermanual.wiki/Root/RGW2400-OD.Program-manual/User-Guide-258965-Page-31.png)
![By using 2 units of RGW linked both with Ethernet, each RGW is enable to be used with different wireless channels, so that generally an actual rate increases than relaying with a single RGW. 4.2 Fire Wall 4.2.1 IP Filter The syntax of IP filter rule is explained in the previous chapter, but terms of each parameter with examples are mentioned here: Once more, syntax of filter rule is indicated: filter add number action inout [log level facility.level] [quick] [on interface] [proto proto] [from[!] address [port] to [!] address [port]][flags][with] [keep][group] Each filter rule has a number, and IP packet received by RGW is assessed in order by all rules. And, it is processed accordingly to finally matched rule ( There are exceptions which is mentioned later). The IP filter of RGW is set to default permit (pass). In other words, a packet do not matches to any rule is permitted. In addition, filter number having order and rule sequence to set RGW is an independent one. * For action, set "pass" or "block", and when it matches the rule specify action of either pass or cancel. * For inout, set "in" or "out", and specify either packet going in RGW or going out of RGW. filter add 10 block in from any to any filter add 11 pass in from any to any](https://usermanual.wiki/Root/RGW2400-OD.Program-manual/User-Guide-258965-Page-44.png)