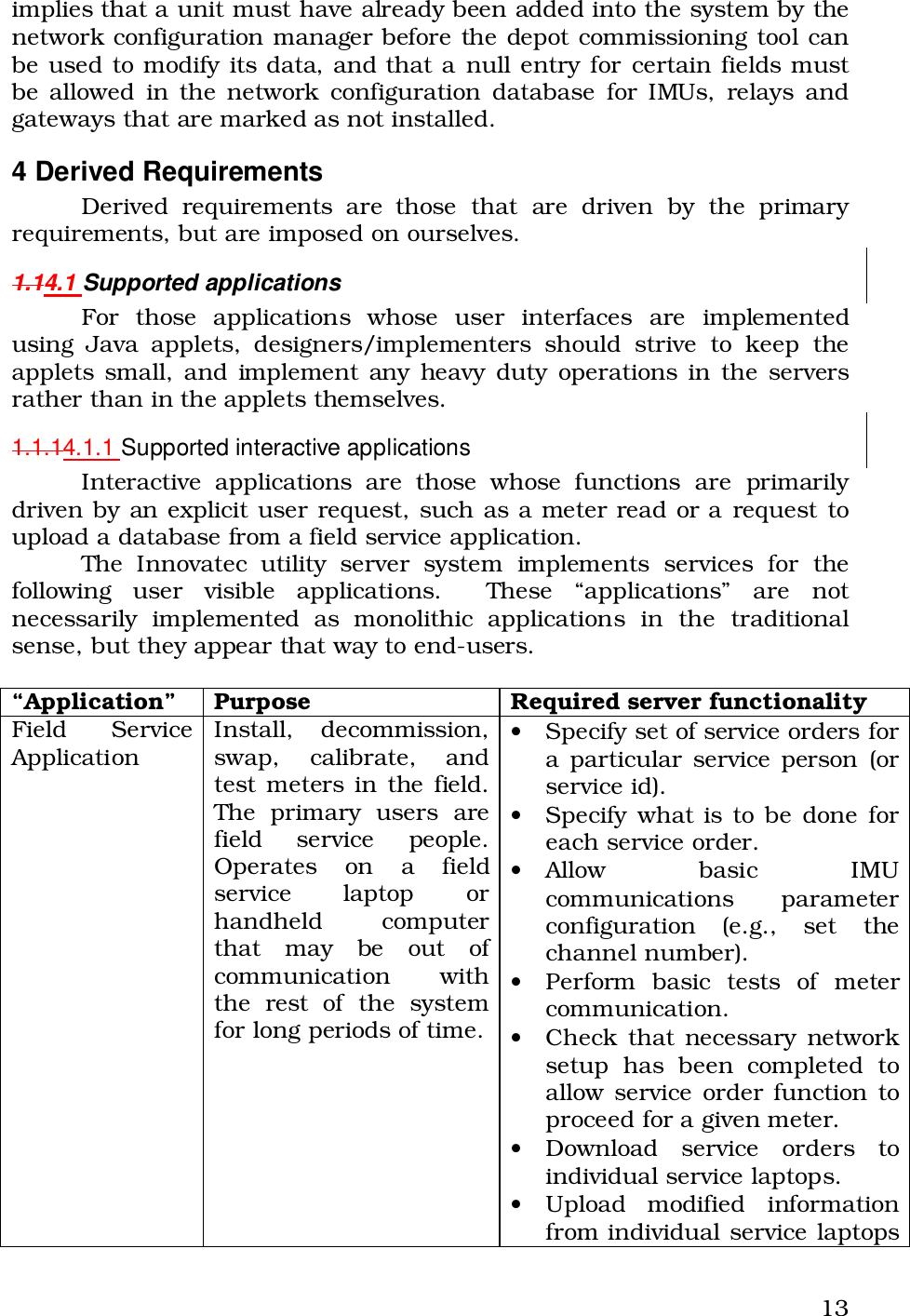
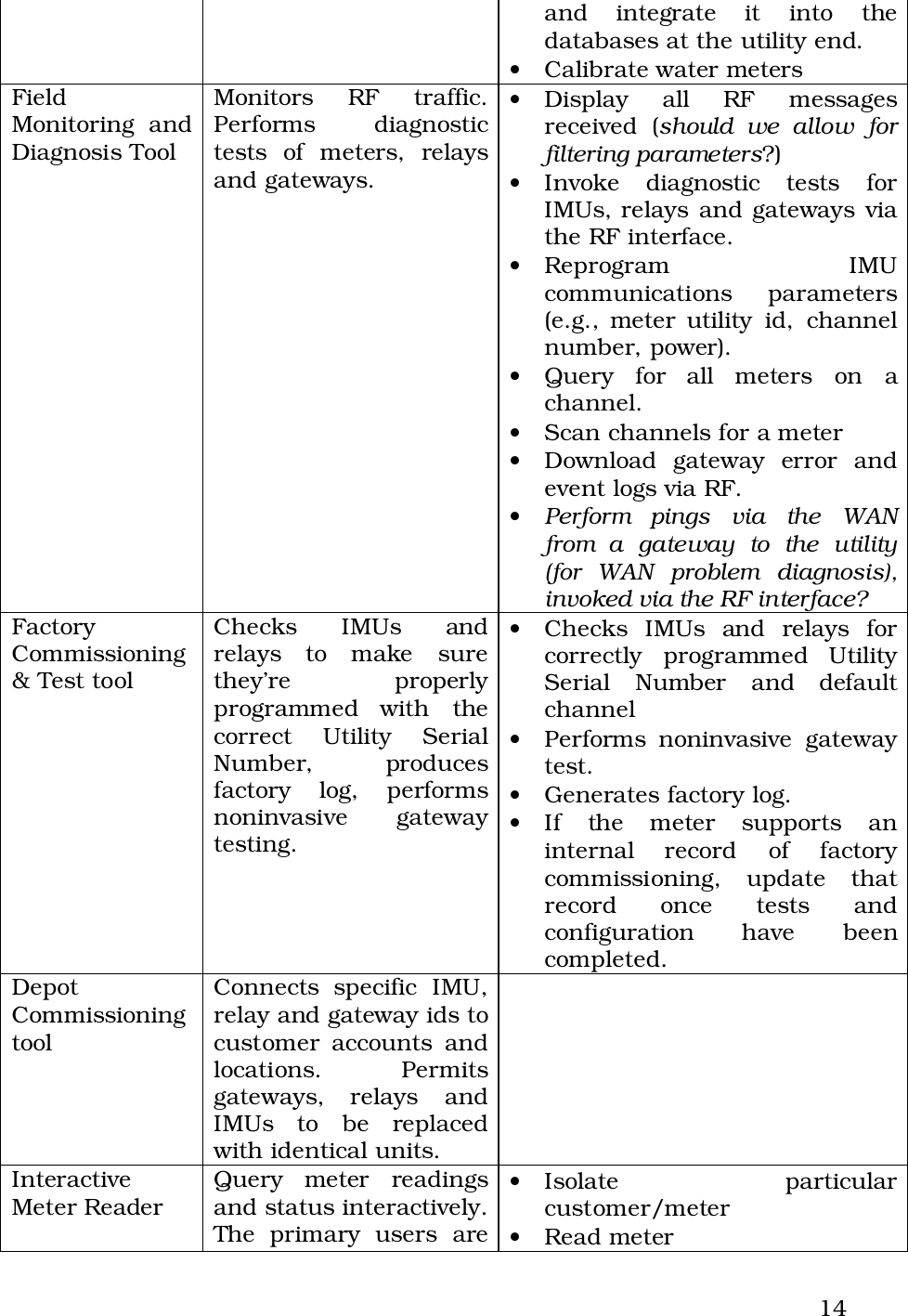
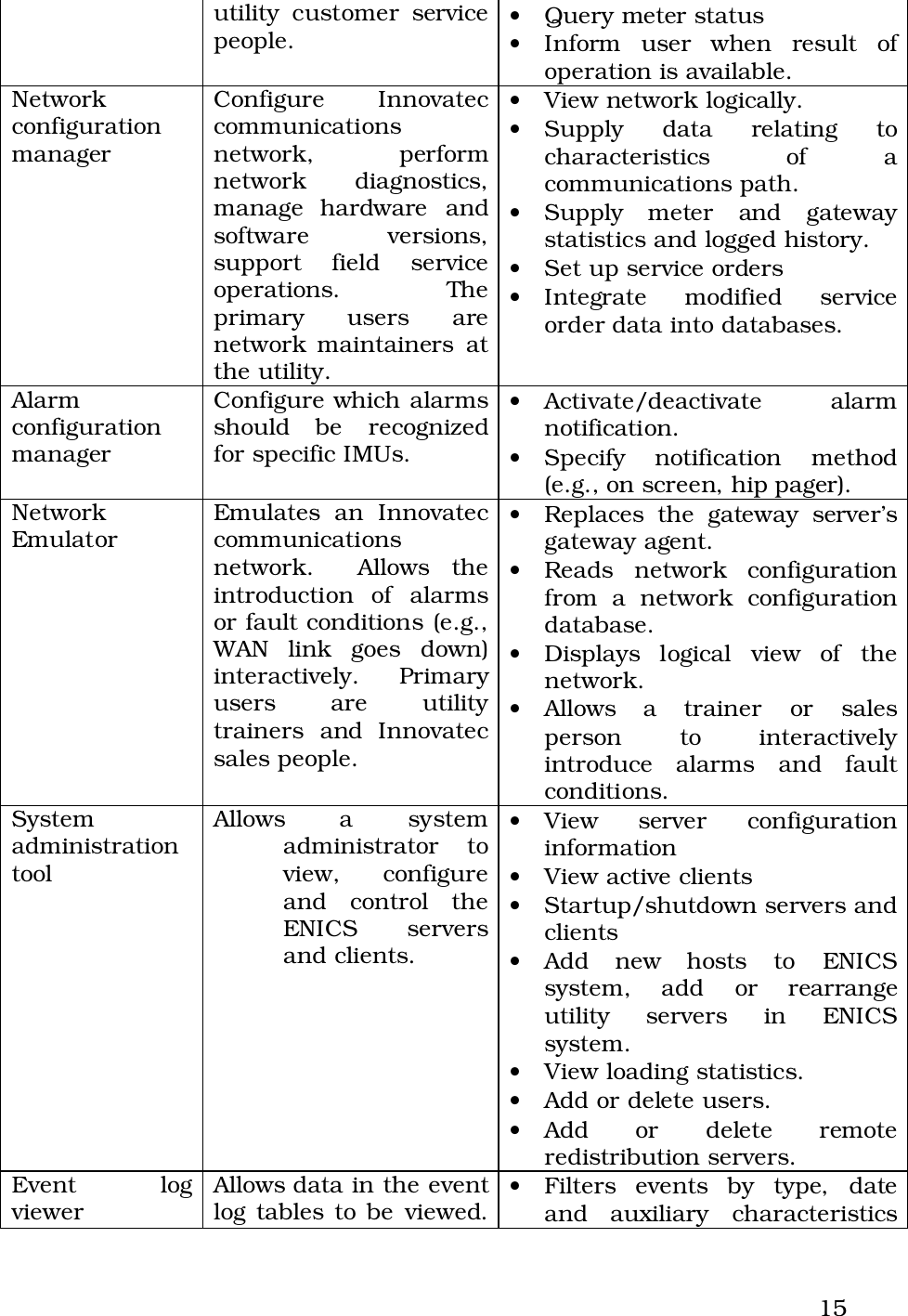
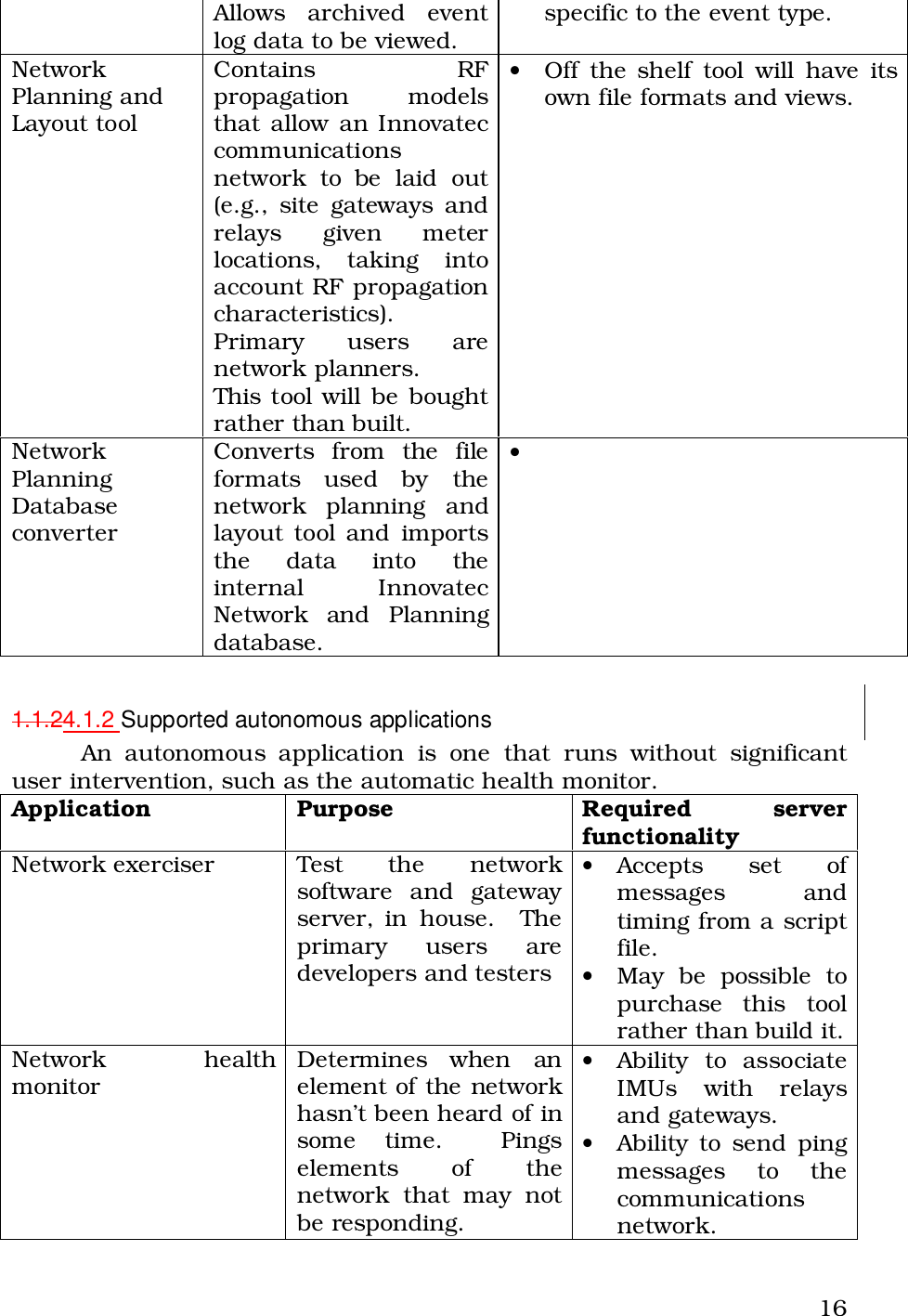
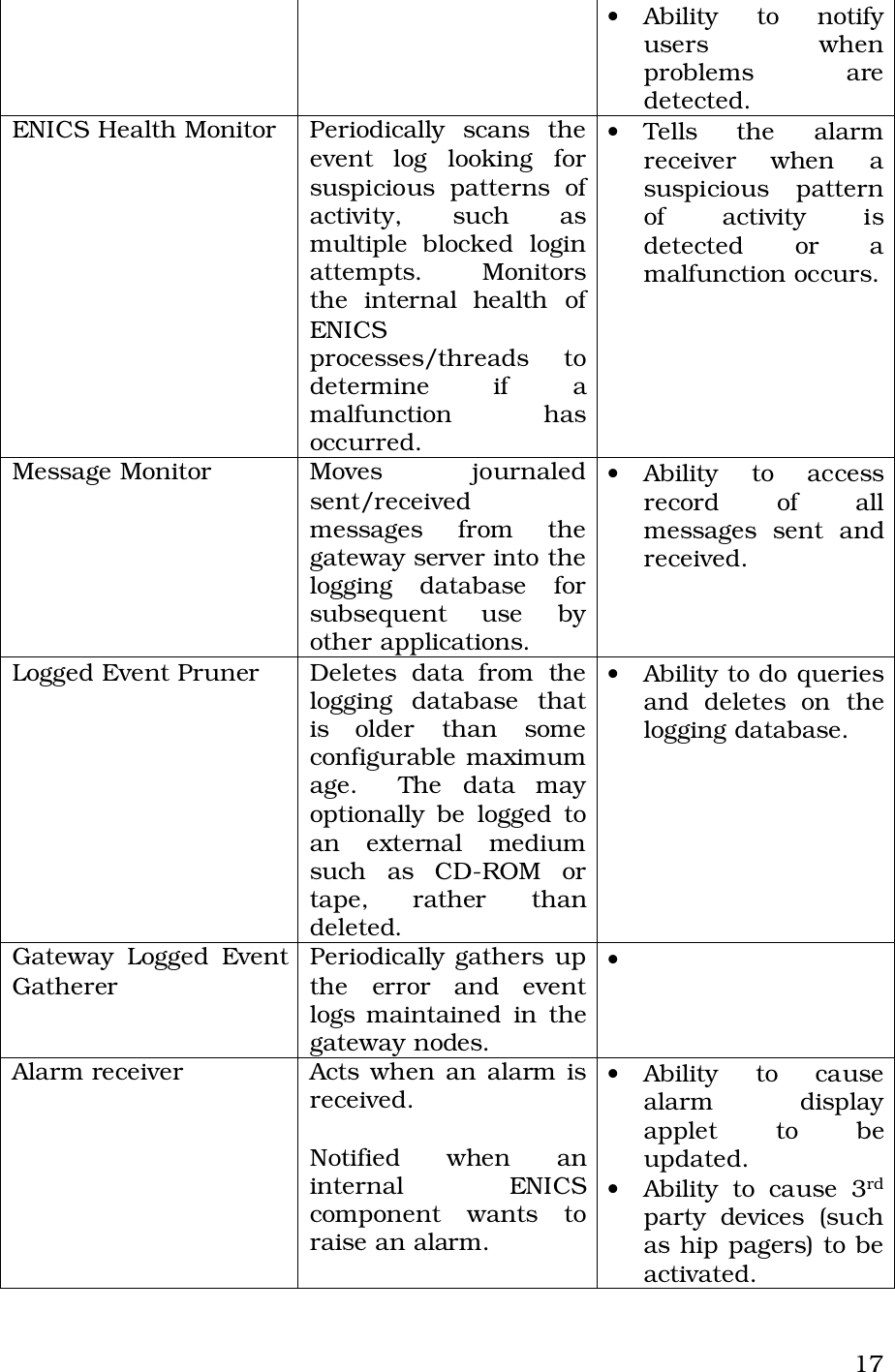
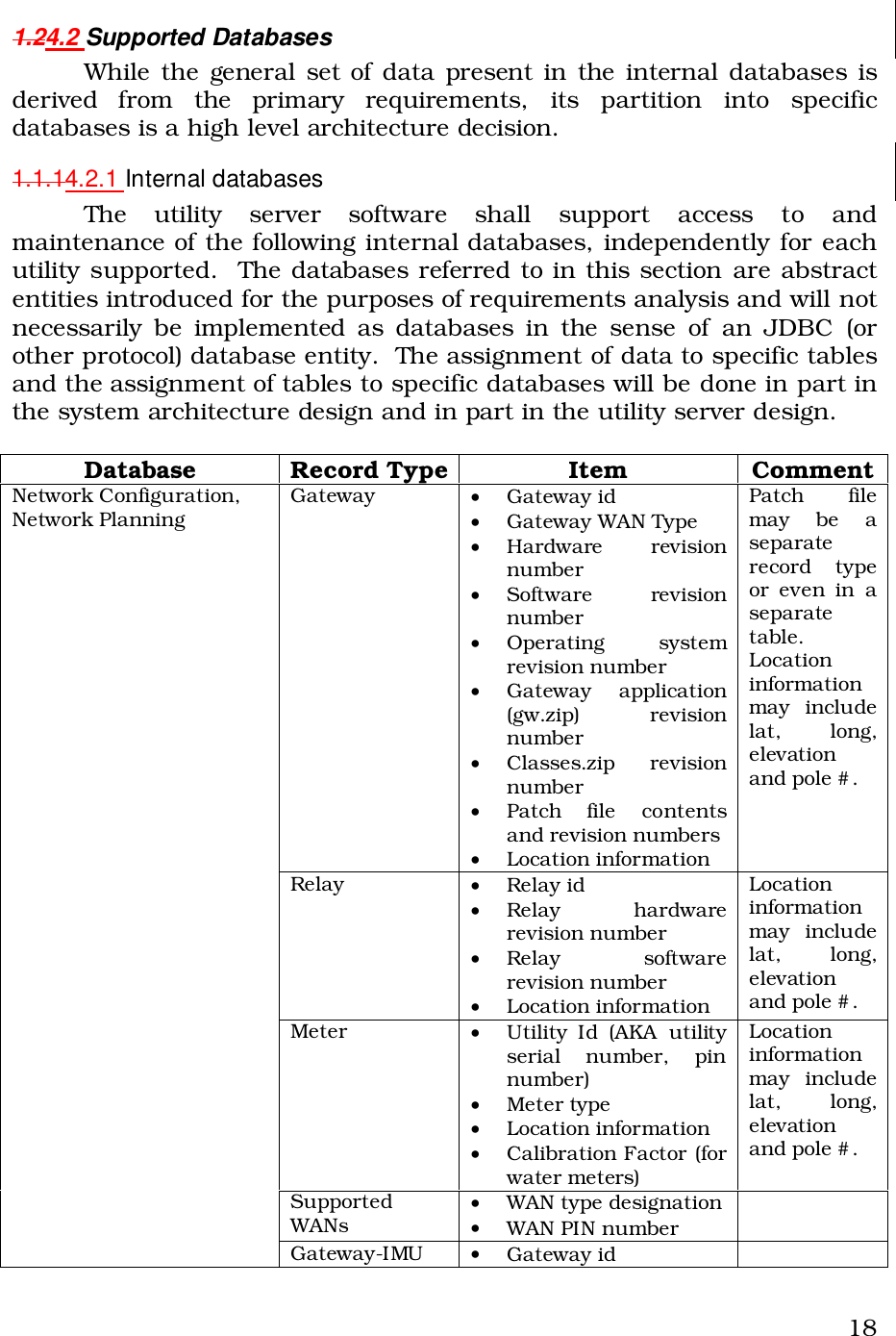
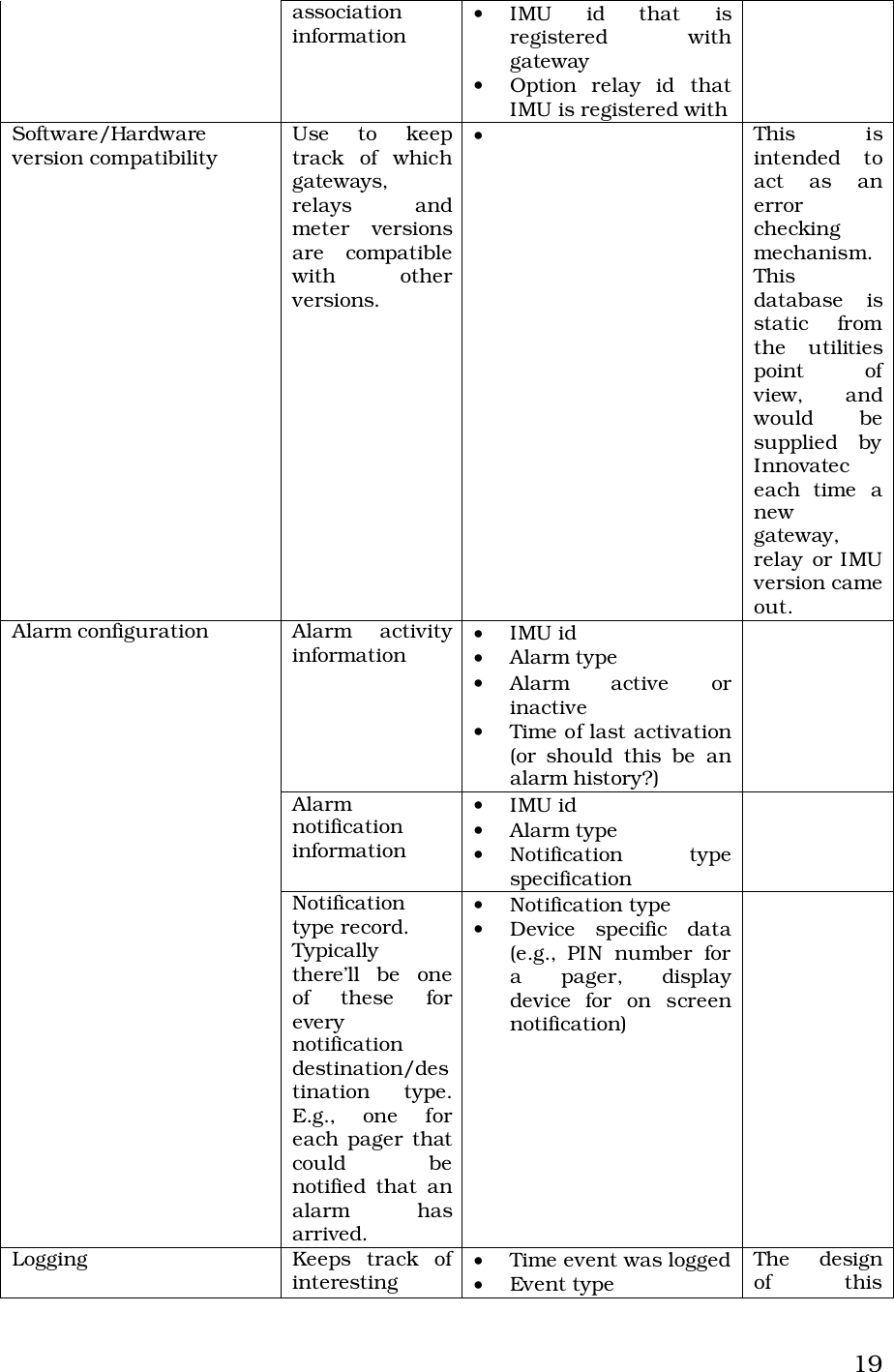
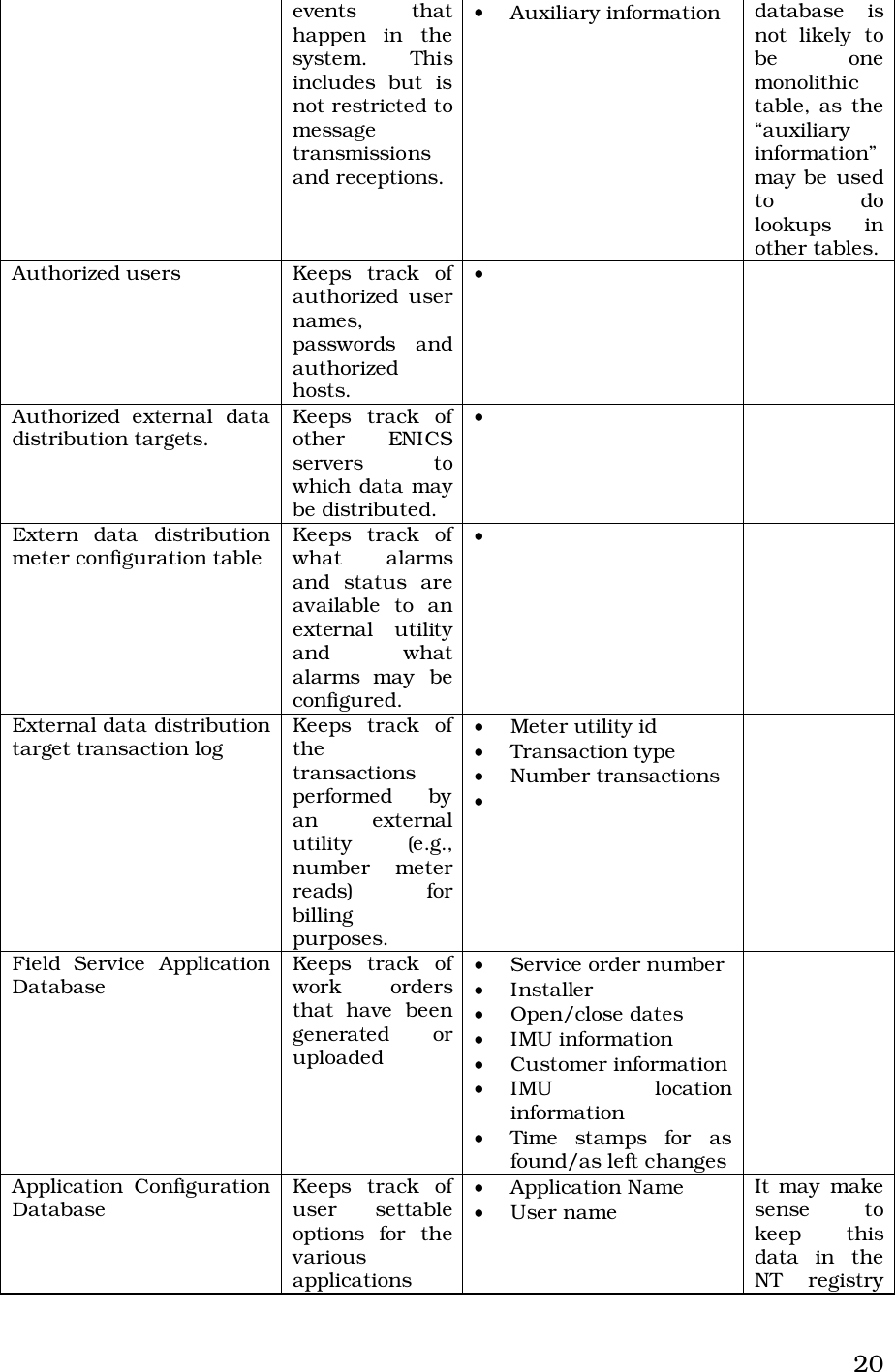
Itron 920 Gateway User Manual Operational Instructions ulitlity software
Silver Spring Networks Gateway Operational Instructions ulitlity software
Itron >
Contents
- 1. User Manual
- 2. Operational Instructions(ulitlity software....?)
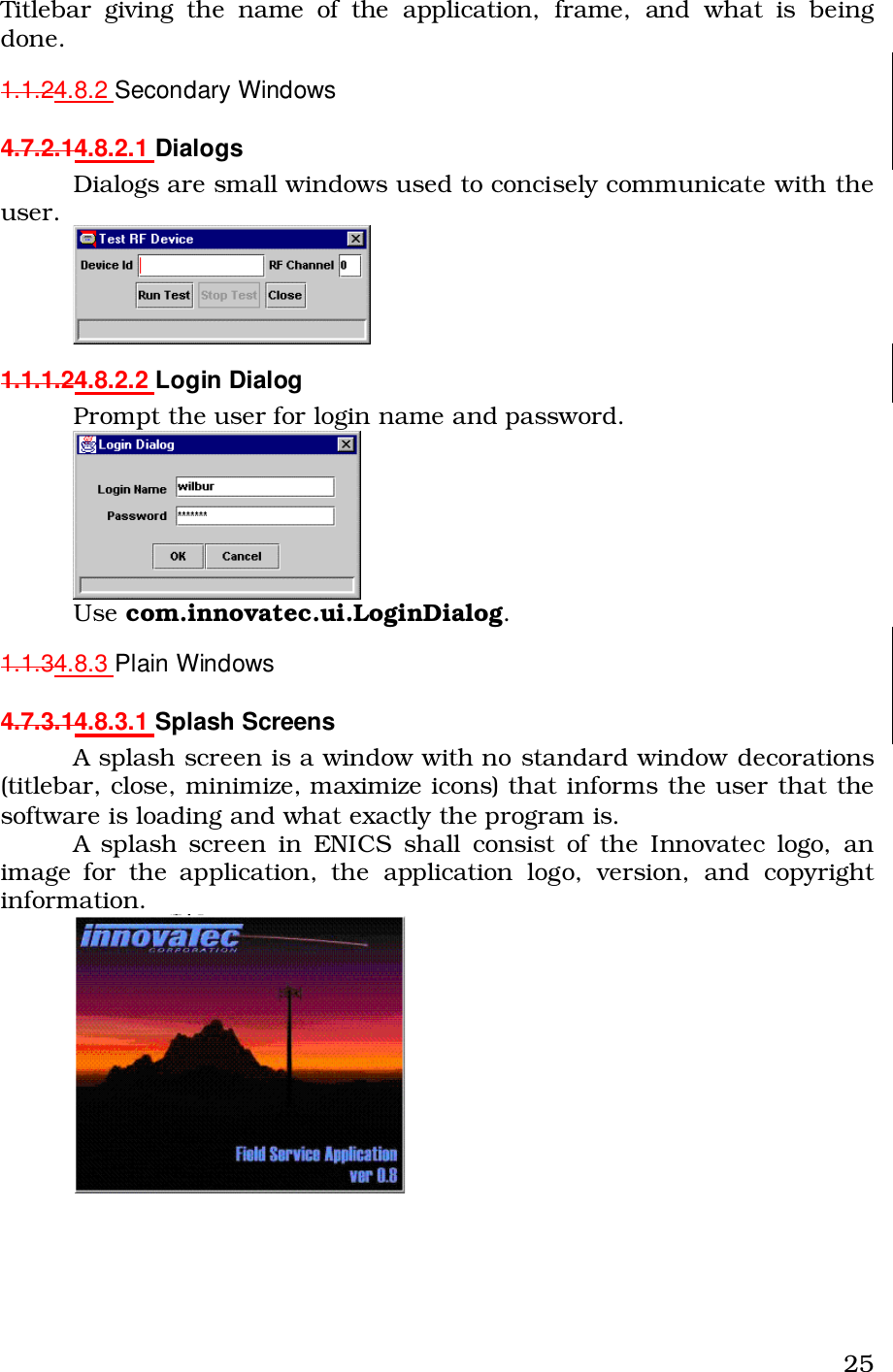
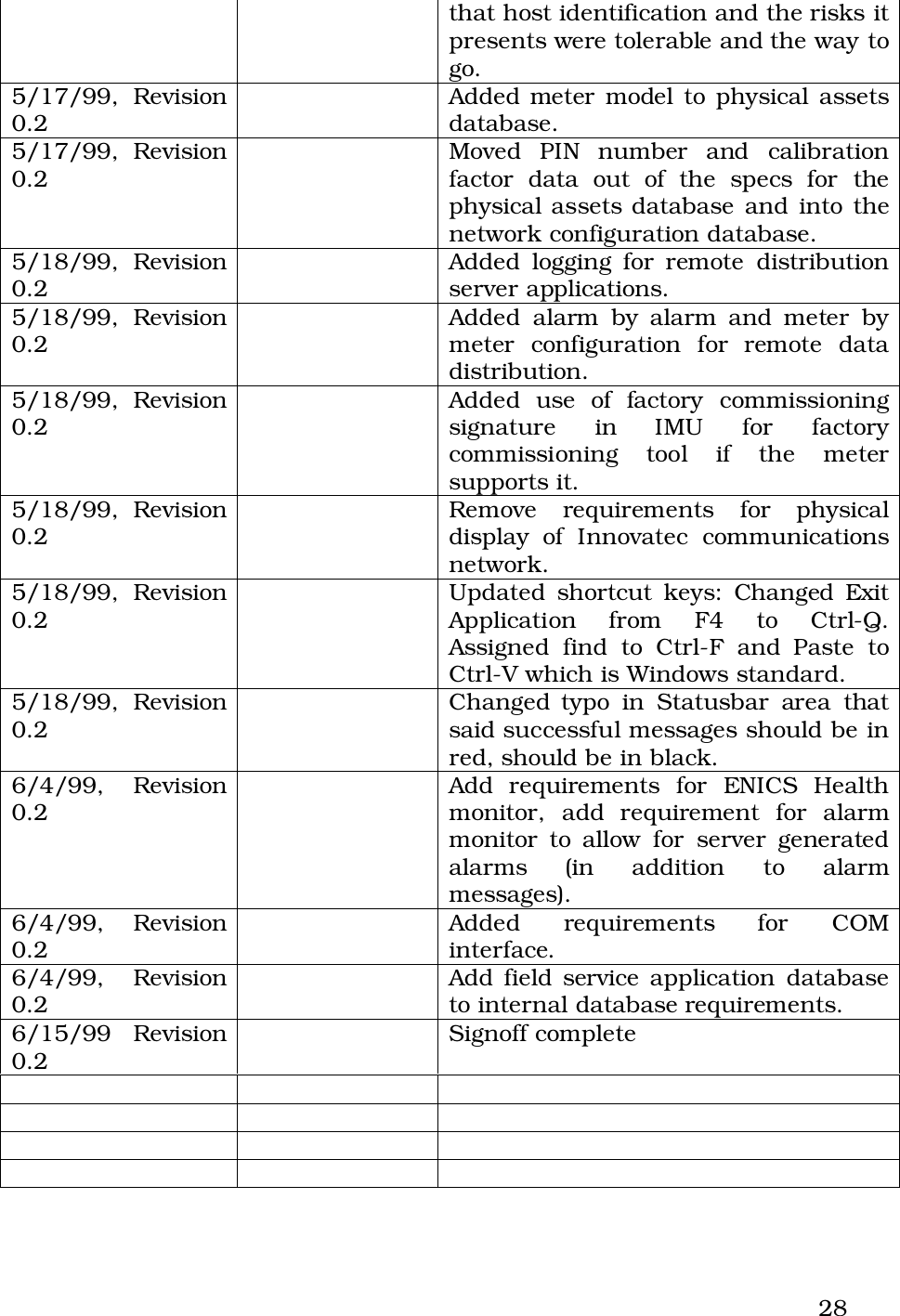
Operational Instructions(ulitlity software....?)