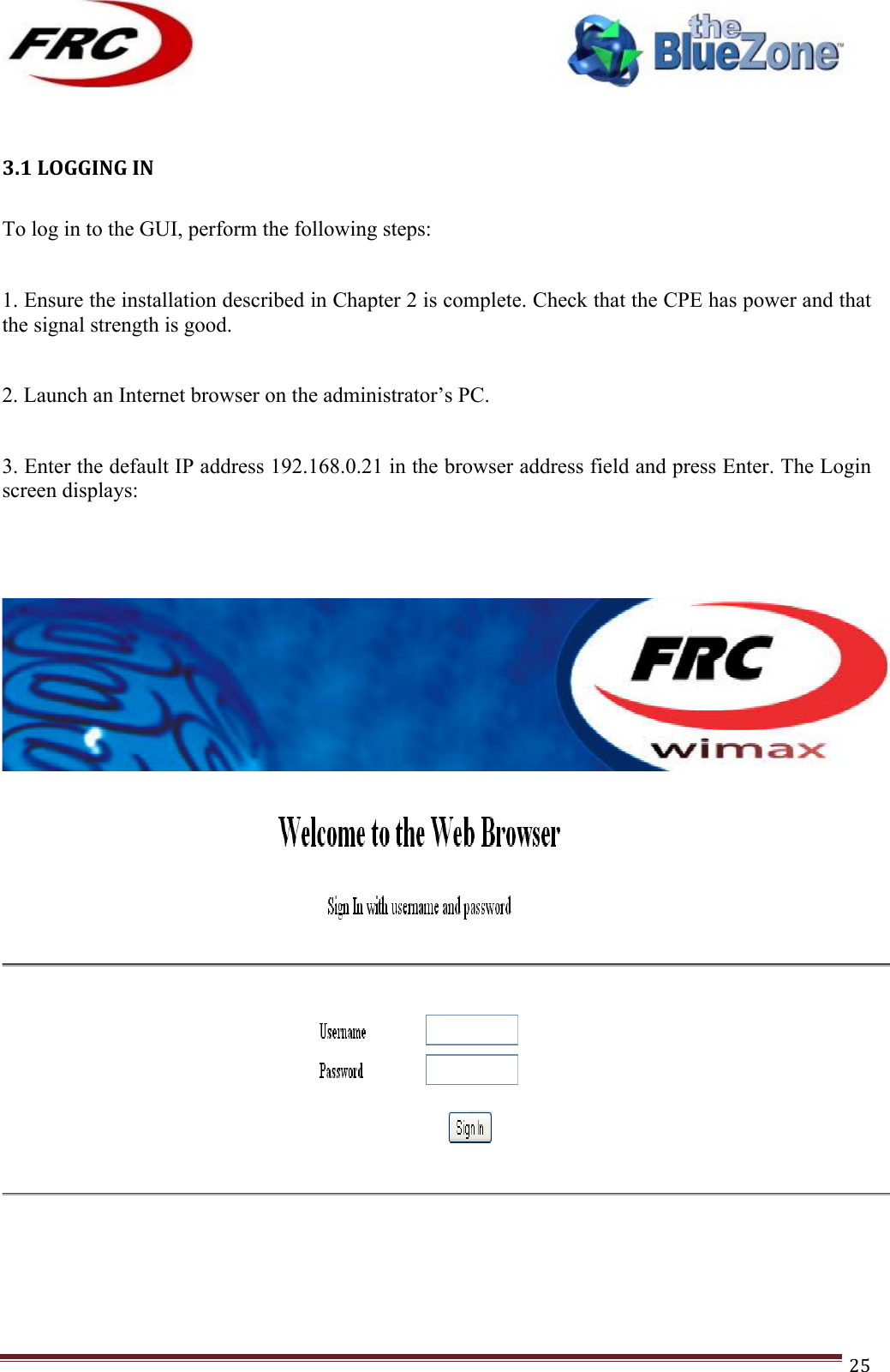
FRC Internet CPEMAXOD365 CPE 3.65GHz Outdoor User Manual FRC WiMAX CPE UserManual V 3 1
FRC Internet Products LLC CPE 3.65GHz Outdoor FRC WiMAX CPE UserManual V 3 1
Contents
- 1. (CPEMax-365)UserMan-(P1-P24)_20120423
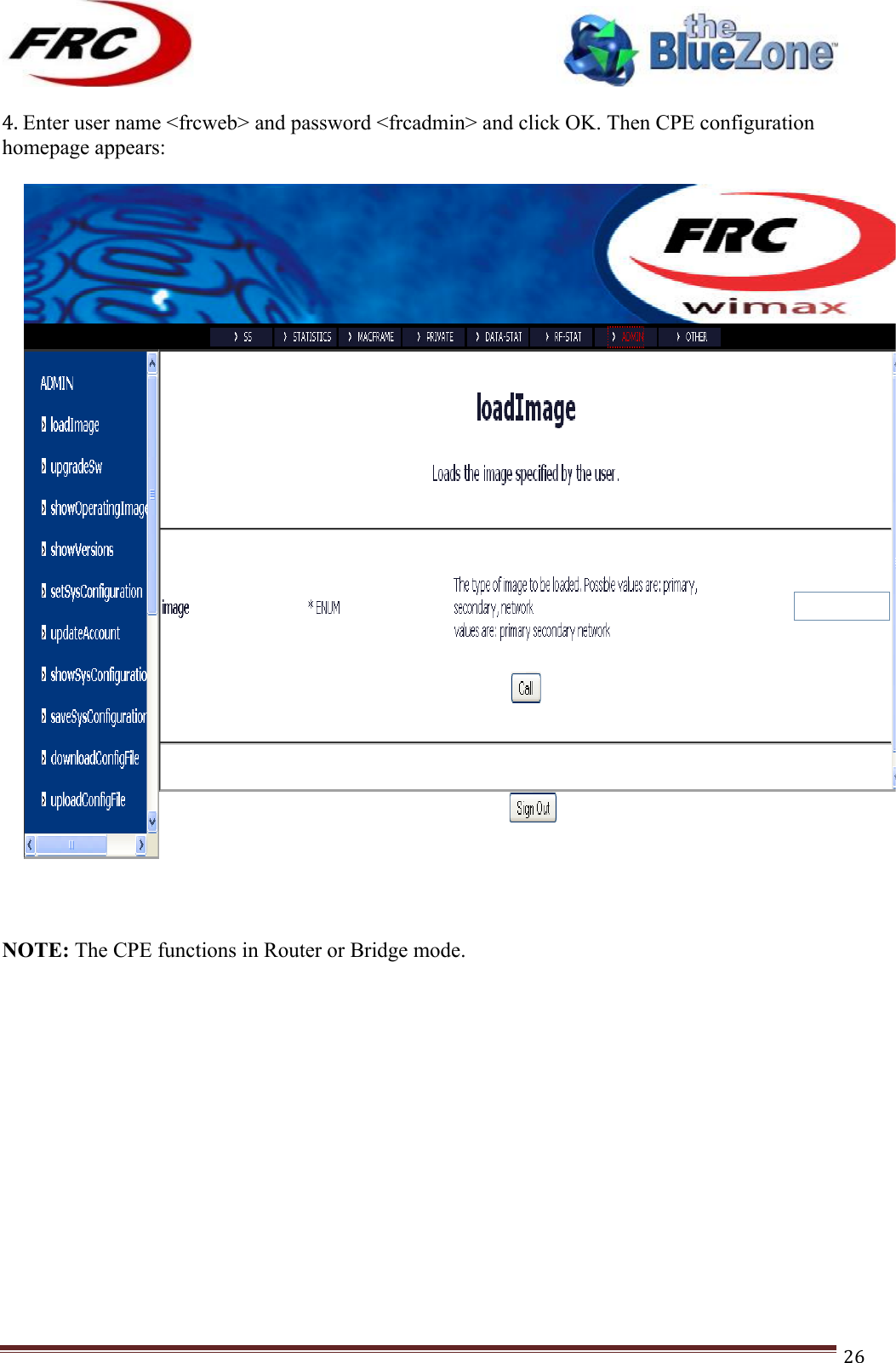
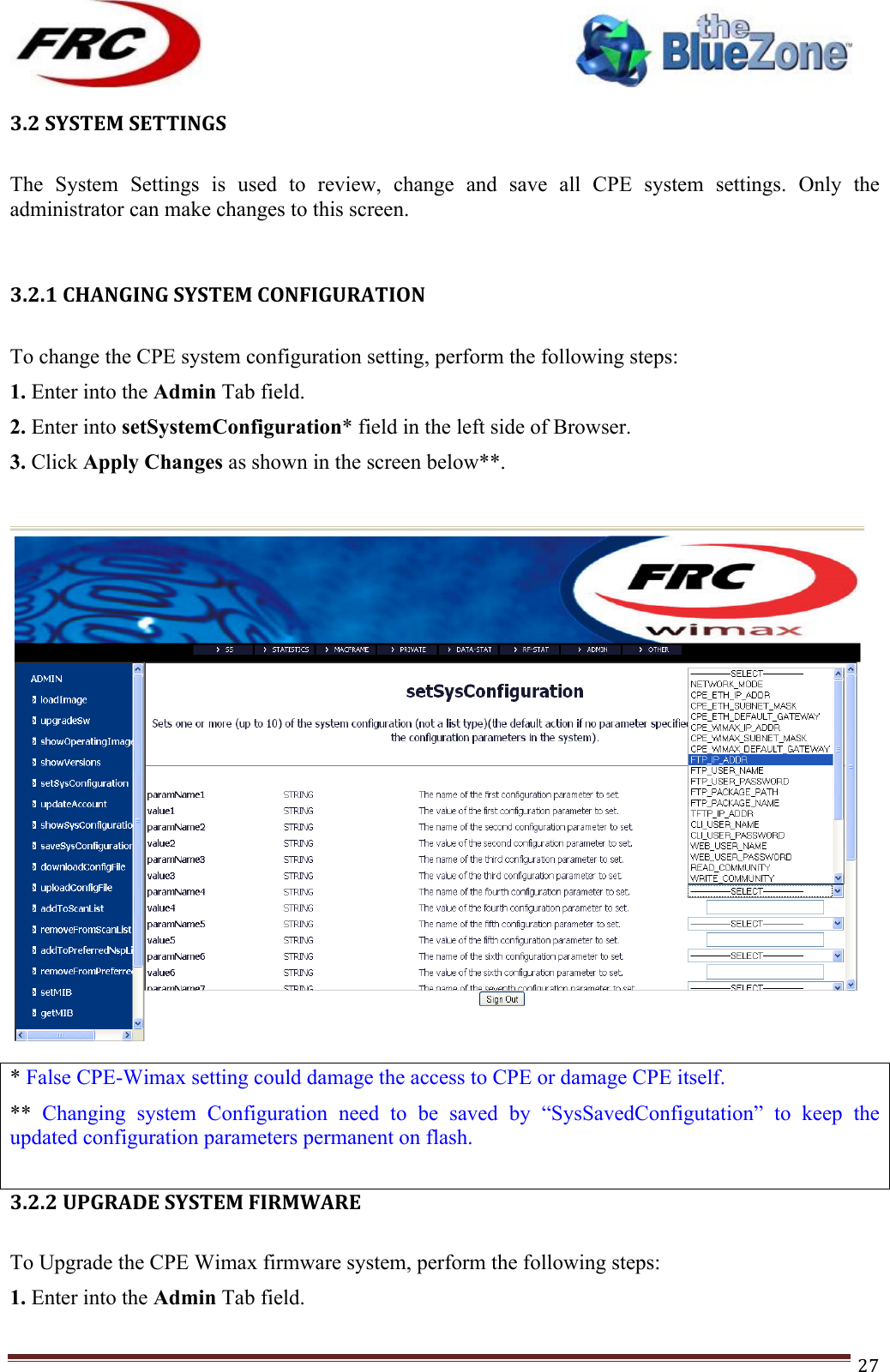
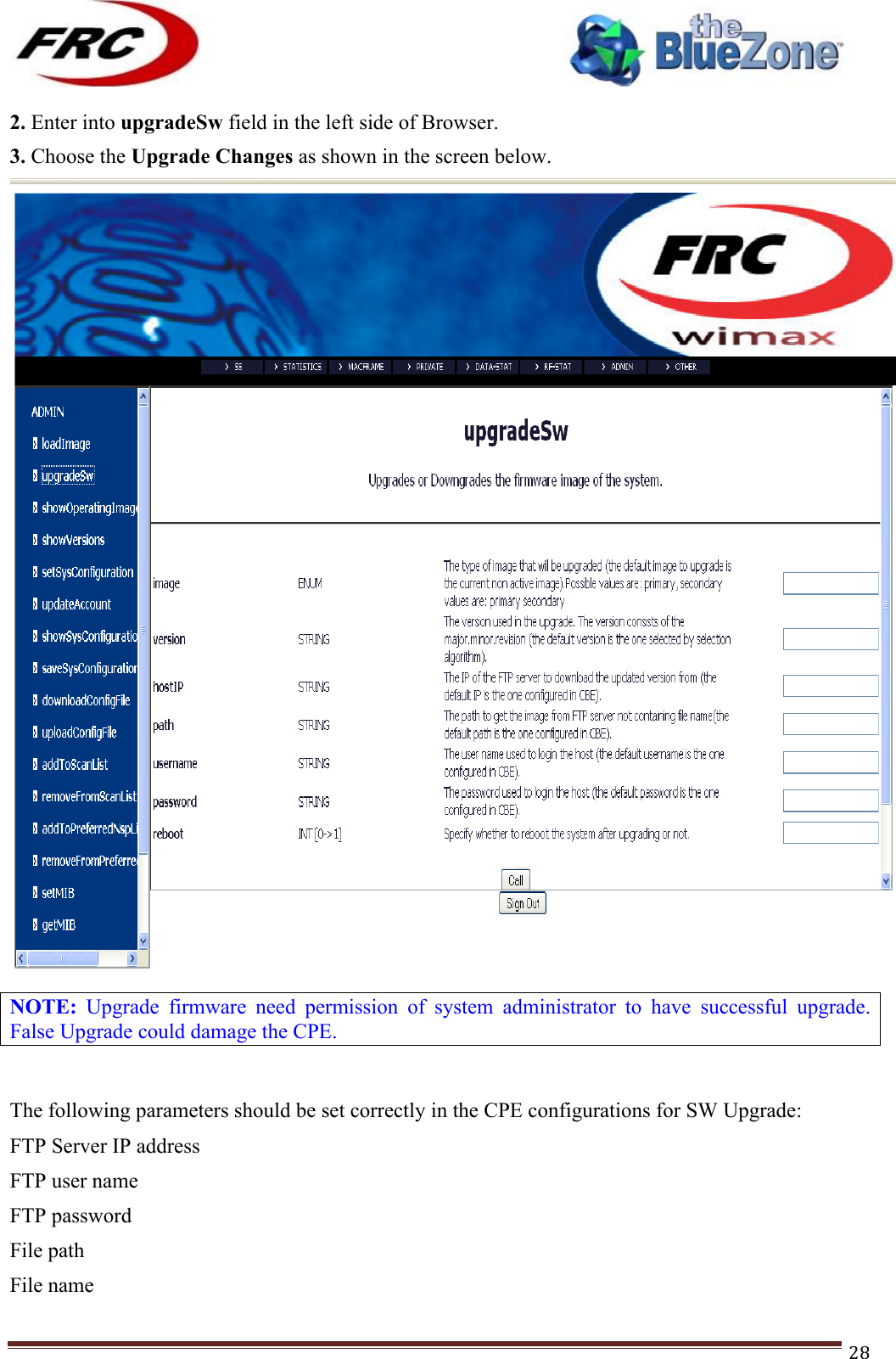
- 2. (CPEMax-365)UserMan-(P25-P65)_20120423
(CPEMax-365)UserMan-(P25-P65)_20120423