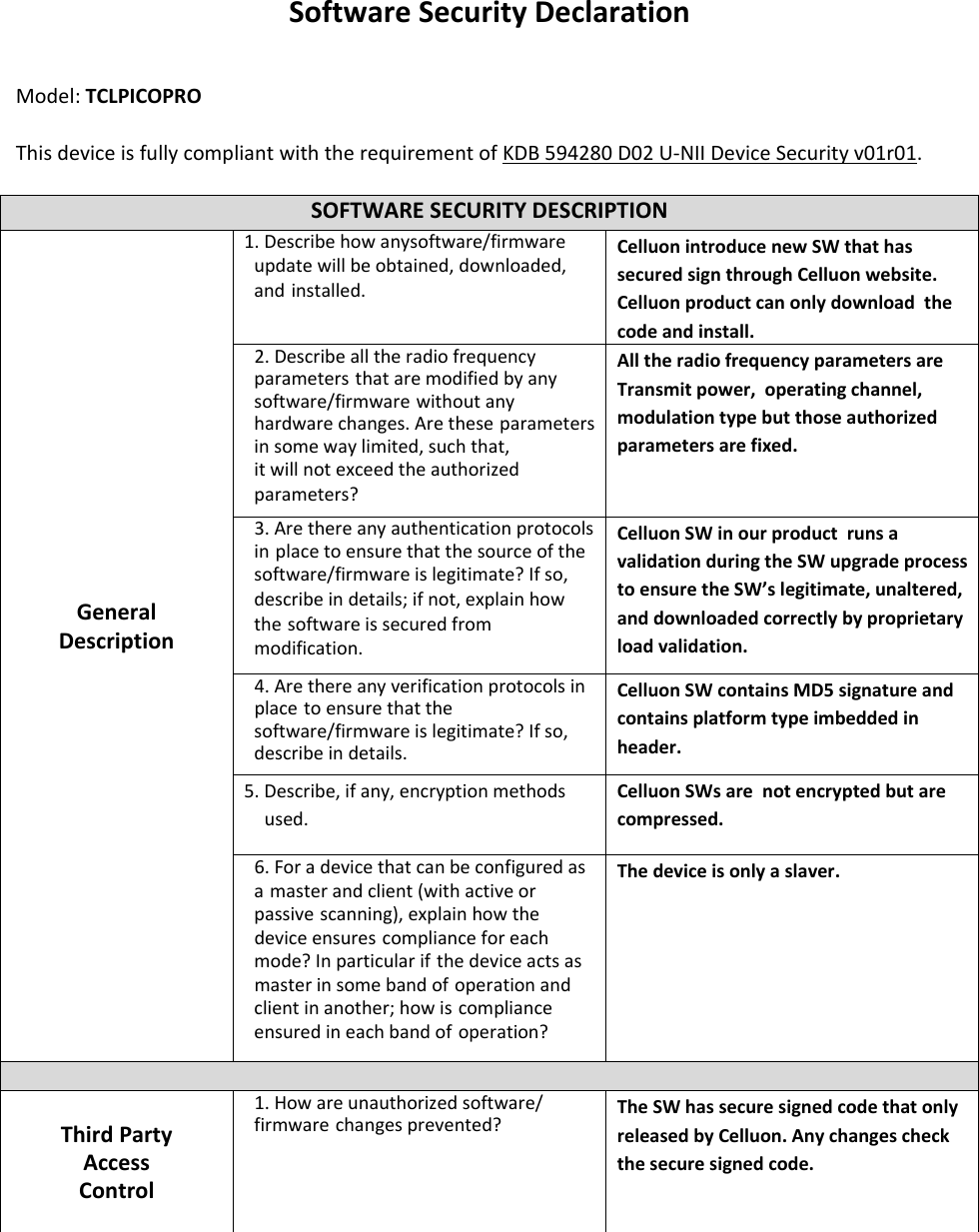
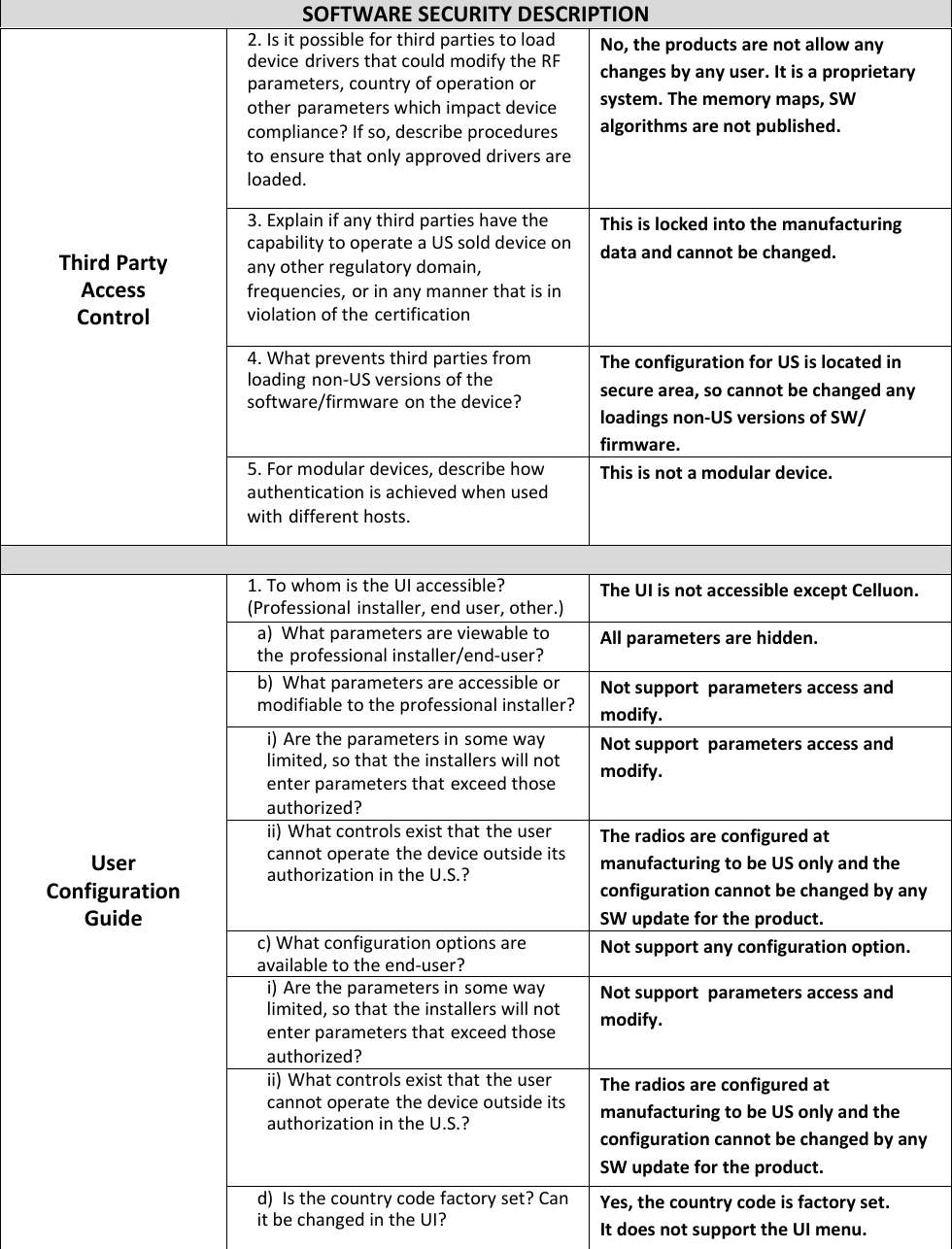
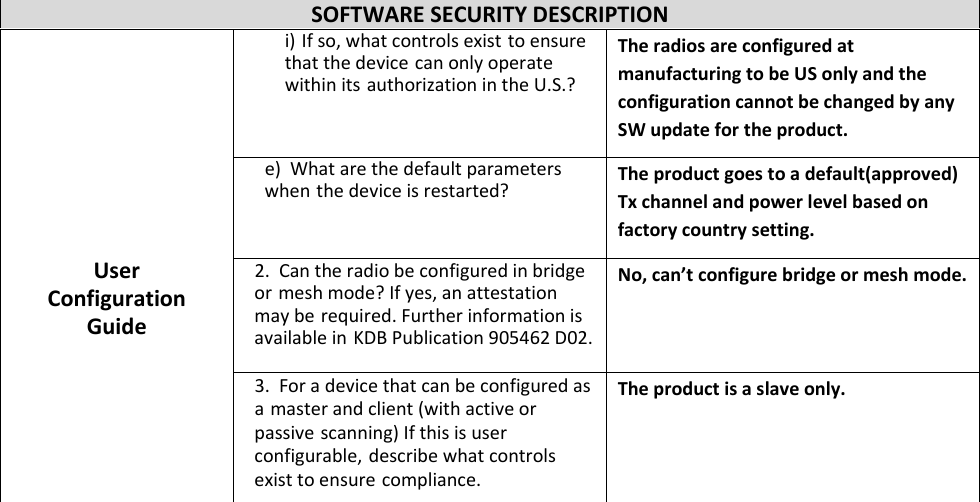
CELLUON PICOPRO Pico projector User Manual Software Security Procedures
CELLUON, INC. Pico projector Software Security Procedures
CELLUON >
Contents
- 1. User Manual
- 2. User Manual Software Security Procedures
User Manual Software Security Procedures